[ad_1]
A new backdoor associated with a malware downloader named Wslink has been discovered, with the tool likely used by the notorious North Korea-aligned Lazarus Group, new findings reveal.
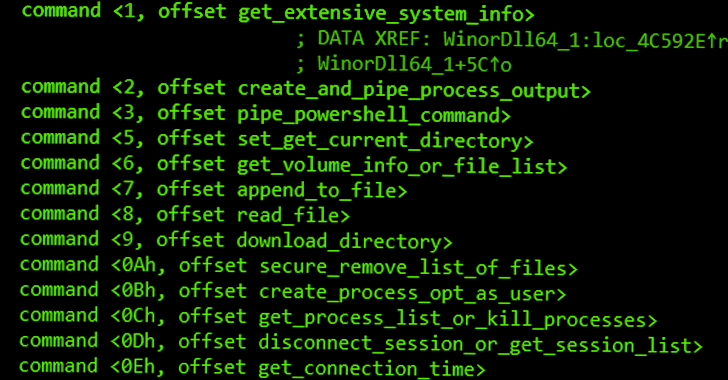
The payload, dubbed WinorDLL64 by ESET, is a fully-featured implant that can exfiltrate, overwrite, and delete files; execute PowerShell commands; and obtain comprehensive information about the underlying machine.
Its other features comprise listing active sessions, creating and terminating processes, enumerating drives, and compressing directories.
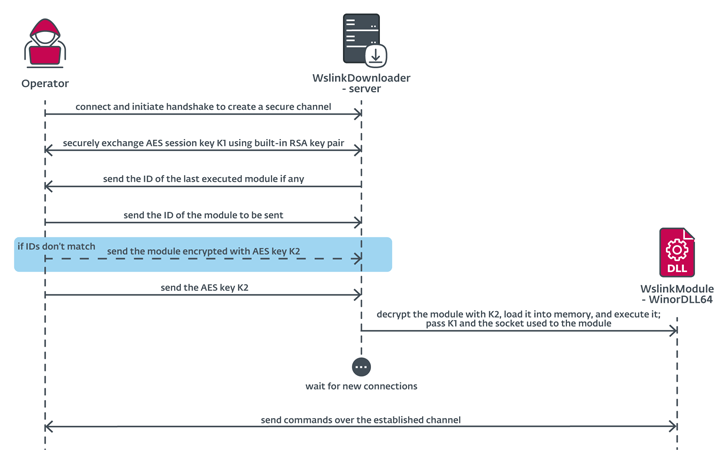
Wslink was first documented by the Slovak cybersecurity firm in October 2021, describing it as a “simple yet remarkable” malware loader that’s capable of executing received modules in memory.
“The Wslink payload can be leveraged later for lateral movement, due to its specific interest in network sessions,” ESET researcher Vladislav Hrčka said. “The Wslink loader listens on a port specified in the configuration and can serve additional connecting clients, and even load various payloads.”
Intrusions leveraging the malware are said to be highly targeted owing to the fact that only a handful of detections have been observed to date in Central Europe, North America, and the Middle East.
In March 2022, ESET elaborated on the malware’s use of an “advanced multi-layered virtual machine” obfuscator to evade detection and resist reverse engineering.
The links to Lazarus Group stem from overlaps in behavior and code to that of previous campaigns – Operation GhostSecret and Bankshot – which have been attributed to the advanced persistent threat.
This includes similarities with the GhostSecret samples detailed by McAfee in 2018, which come with a “data-gathering and implant-installation component” that runs as a service, mirroring the same behavior of Wslink.
ESET said the payload was uploaded to the VirusTotal malware database from South Korea, where some of the victims are located, adding credence to the Lazarus involvement.
The findings are once again demonstrative of the vast arsenal of hacking tools employed by the Lazarus Group to infiltrate its targets.
“Wslink’s payload is dedicated to providing means for file manipulation, execution of further code, and obtaining extensive information about the underlying system that possibly can be leveraged later for lateral movement,” ESET said.
[ad_2]
Source link