[ad_1]
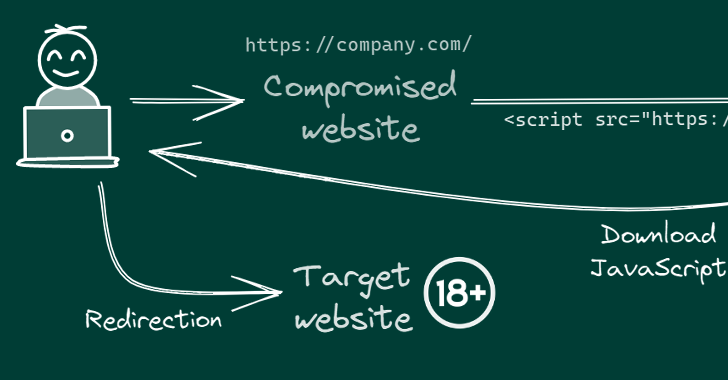
A widespread malicious cyber operation has hijacked thousands of websites aimed at East Asian audiences to redirect visitors to adult-themed content since early September 2022.
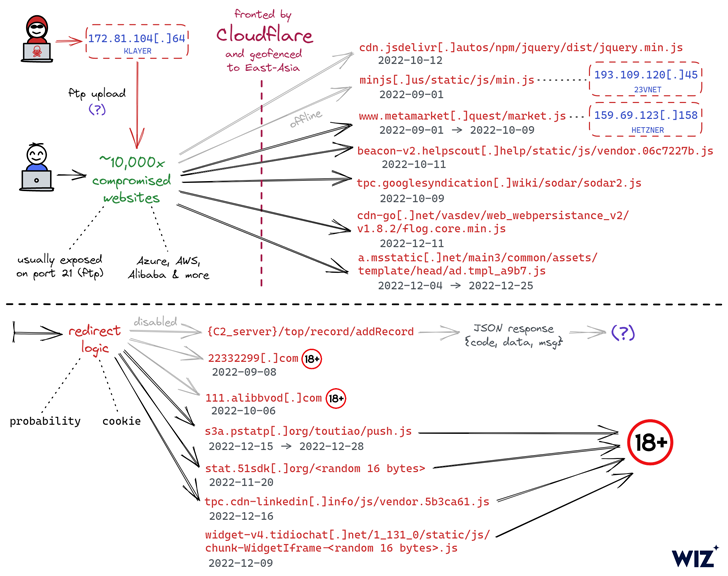
The ongoing campaign entails injecting malicious JavaScript code to the hacked websites, often connecting to the target web server using legitimate FTP credentials the threat actor previously obtained via an unknown method.
“In many cases, these were highly secure auto-generated FTP credentials which the attacker was somehow able to acquire and leverage for website hijacking,” Wiz said in a report published this month.
The fact that the breached websites – owned by both small firms and multinational corporations – utilize different tech stacks and hosting service providers has made it difficult to trace a common attack vector, the cloud security company noted.
That having said, one of the common denominators between the websites is that a majority of them are either hosted in China or hosted in a different country but are primed for Chinese users.
What’s more, the URLs hosting the rogue JavaScript code are geofenced to limit its execution in certain East Asian countries.
There are also indications that the campaign has set its sights on Android as well, with the redirection script leading visitors to gambling websites that urge them to install an app (APK package name “com.tyc9n1999co.coandroid“).
The identity of the threat actor is unknown as yet, and although their precise motives are yet to be identified, it is suspected that the goal is to carry out ad fraud and SEO manipulation, or alternatively, drive inorganic traffic to these websites.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
Another notable aspect of the attacks is the absence of phishing, web skimming, or malware infection.
“We remain unsure as to how the threat actor has been gaining initial access to so many websites, and we have yet to identify any significant commonalities between the impacted servers other than their usage of FTP,” researchers Amitai Cohen and Barak Sharoni said.
“Although it’s unlikely that the threat actor is using a 0-day vulnerability given the apparently low sophistication of the attack, we can’t rule this out as an option.”
[ad_2]
Source link