[ad_1]
An advanced persistent threat (APT) group that has a track record of targeting India and Afghanistan has been linked to a new phishing campaign that delivers Action RAT.
According to Cyble, which attributed the operation to SideCopy, the activity cluster is designed to target the Defence Research and Development Organization (DRDO), the research and development wing of India’s Ministry of Defence.
Known for emulating the infection chains associated with SideWinder to deliver its own malware, SideCopy is a threat group of Pakistani origin that shares overlaps with Transparent Tribe. It has been active since at least 2019.
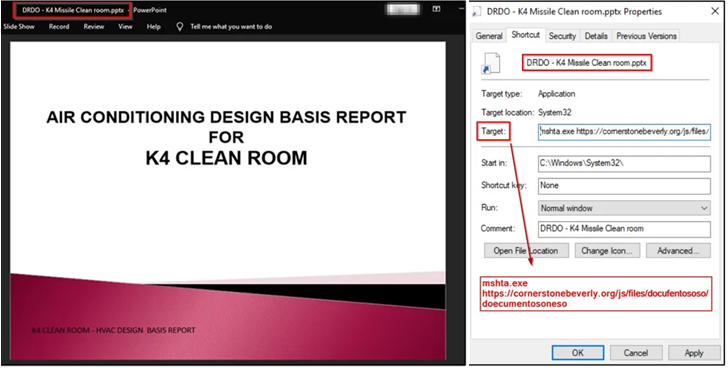
Attack chains mounted by the group involve using spear-phishing emails to gain initial access. These messages come bearing a ZIP archive file that contains a Windows shortcut file (.LNK) masquerading as information about the K-4 ballistic missile developed by DRDO.
Executing the .LNK file leads to the retrieval of an HTML application from a remote server, which, in turn, displays a decoy presentation, while also stealthily deploying the Action RAT backdoor.
The malware, in addition to gathering information about the victim machine, is capable of running commands sent from a command-and-control (C2) server, including harvesting files and dropping follow-on malware.
Also deployed is a new information-stealing malware referred to as AuTo Stealer that’s equipped to gather and exfiltrate Microsoft Office files, PDF documents, database and text files, and images over HTTP or TCP.
“The APT group continuously evolves its techniques while incorporating new tools into its arsenal,” Cyble noted.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
This is not the first time SideCopy has employed Action RAT in its attacks directed against India. In December 2021, Malwarebytes disclosed a set of intrusions that breached a number of ministries in Afghanistan and a shared government computer in India to steal sensitive credentials.
The latest findings arrive a month after the adversarial crew was spotted targeting Indian government agencies with a remote access trojan dubbed ReverseRAT.
[ad_2]
Source link