[ad_1]
Ransomware affiliates associated with the Qilin ransomware-as-a-service (RaaS) scheme earn anywhere between 80% to 85% of each ransom payment, according to new findings from Group-IB.
The cybersecurity firm said it was able to infiltrate the group in March 2023, uncovering details about the affiliates’ payment structure and the inner workings of the RaaS program following a private conversation with a Qilin recruiter who goes by the online alias Haise.
“Many Qilin ransomware attacks are customized for each victim to maximize their impact,” the Singapore-headquartered company said in an exhaustive report. “To do this, the threat actors can leverage such tactics as changing the filename extensions of encrypted files and terminating specific processes and services.”
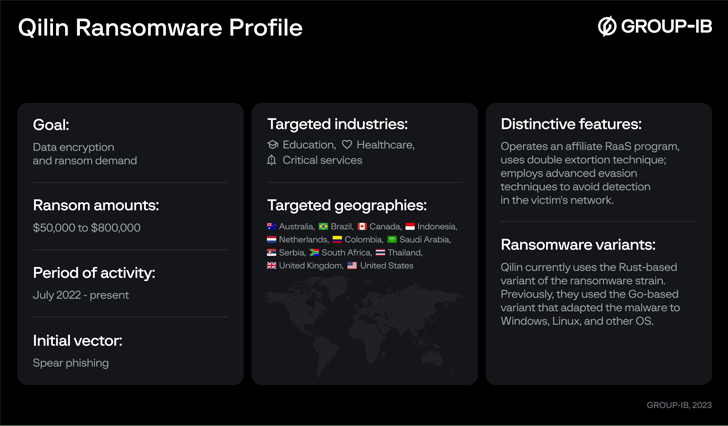
Qilin, also known as Agenda, was first documented by Trend Micro in August 2022, starting off as a Go-based ransomware before switching to Rust in December 2022.
The adoption of Rust is also significant not only because of evasion detection capabilities, but also for the fact that it allows the threat actors to target Windows, Linux, and VMware ESXi servers.
Attacks mounted by the group make use of phishing emails containing malicious links as a means to obtain initial access and encrypt sensitive data, but not before exfiltrating it as part of a double extortion model.
Data from as many as 12 different companies have been posted on Qilin’s data leak portal on the dark web between July 2022 and May 2023.
The victims, which mainly span critical infrastructure, education, and healthcare sectors, are located in Australia, Brazil, Canada, Colombia, France, Japan, Netherlands, Serbia, the U.K., and the U.S.
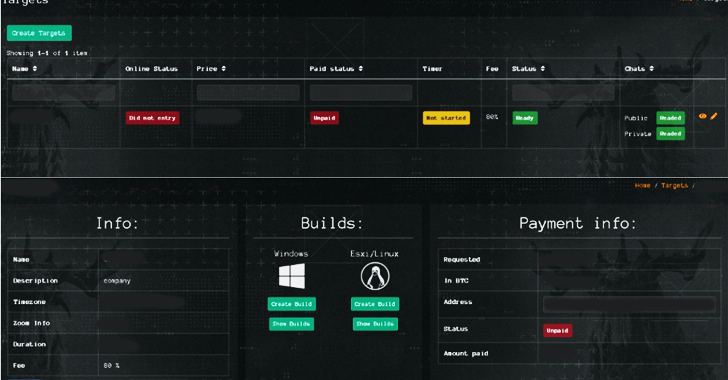
Group-IB said the Qilin actors also provide affiliates – who are recruited to identify targets of interest and stage the attacks – with an administrative panel to effectively oversee various parts of their operations.
“Qilin ransomware group has an affiliate panel divided into sections such as Targets, Blogs, Stuffers, News, Payments, and FAQs to manage and coordinate its network of affiliates,” security researcher Nikolay Kichatov said.
- Targets – A section to configure ransom notes, files, directories, and extensions to be skipped, extensions to be encrypted, processes to be terminated, and the mode of encryption, among others
- Blogs – A section for affiliates to create blog posts with information about attacked companies that have not paid the ransom
- Stuffers – A section for the threat actors to create accounts for other members of the team and manage their privileges
- News – A section to post updates related to their ransomware partnerships (currently blank)
- Payments – A section that contains transaction details, affiliate wallet balances, and options to withdraw illicit proceeds
- FAQs – A section featuring support and documentation information that details the steps to use the ransomware
“Although Qilin ransomware gained notoriety for targeting critical sector companies, they are a threat to organizations across all verticals,” Kichatov said.
“Moreover, the ransomware operator’s affiliate program is not only adding new members to its network, but it is weaponizing them with upgraded tools, techniques, and even service delivery.”
[ad_2]
Source link