[ad_1]
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023.
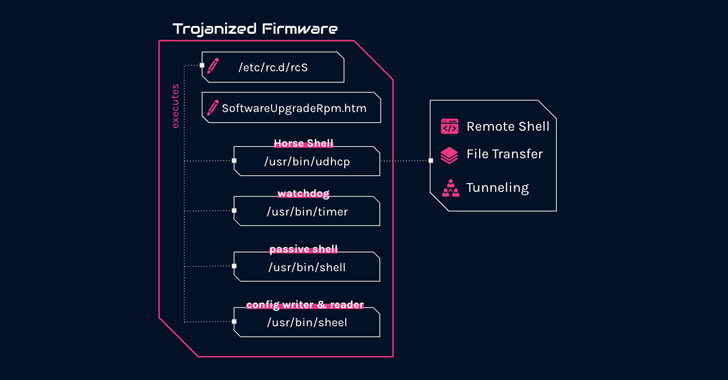
An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.
“The implant features several malicious components, including a custom backdoor named ‘Horse Shell’ that enables the attackers to maintain persistent access, build anonymous infrastructure, and enable lateral movement into compromised networks,” the company said.
“Due to its firmware-agnostic design, the implant’s components can be integrated into various firmware by different vendors.”
The Israeli cybersecurity firm is tracking the threat group under the name Camaro Dragon, which is also known as BASIN, Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.
The exact method used to deploy the tampered firmware images on the infected routers is currently unknown, as is its usage and involvement in actual attacks. It’s suspected that initial access may have been acquired by exploiting known security flaws or brute-forcing devices with default or easily guessable passwords.
What is known is that the C++-based Horse Shell implant provides attackers the ability to execute arbitrary shell commands, upload and download files to and from the router, and relay communication between two different clients.
But in an interesting twist, the router backdoor is believed to target arbitrary devices on residential and home networks, suggesting that the compromised routers are being co-opted into a mesh network with the goal of creating a “chain of nodes between main infections and real command-and-control.”
In relaying communications between infected routers by using a SOCKS tunnel, the idea is to introduce an additional layer of anonymity and conceal the final server, as each node in the chain contains information only about the nodes preceding and succeeding it.
Put differently, the methods obscure the origin and destination of the traffic in a manner analogous to TOR, making it a lot more challenging to detect the scope of the attack and disrupt it.
“If one node in the chain is compromised or taken down, the attacker can still maintain communication with the C2 by routing traffic through a different node in the chain,” the researchers explained.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
That said, this is not the first time China-affiliated threat actors have relied on a network of compromised routers to meet their strategic objectives.
In 2021, the National Cybersecurity Agency of France (ANSSI) detailed an intrusion set orchestrated by APT31 (aka Judgement Panda or Violet Typhoon) that leveraged a piece of advanced malware known as Pakdoor (or SoWat) to allow the infected routers to communicate with each other.
“The discovery is yet another example of a long-standing trend of Chinese threat actors to exploit internet-facing network devices and modify their underlying software or firmware,” the researchers said.
[ad_2]
Source link