[ad_1]
Ransomware actors and cryptocurrency scammers have joined nation-state actors in abusing cloud mining services to launder digital assets, new findings reveal.
“Cryptocurrency mining is a crucial part of our industry, but it also holds special appeal to bad actors, as it provides a means to acquire money with a totally clean on-chain original source,” blockchain analytics firm Chainalysis said in a report shared with The Hacker News.
Earlier this March, Google Mandiant disclosed North Korea-based APT43’s use of the hash rental and cloud mining services to obscure the forensic trail and wash the stolen cryptocurrency “clean.”
Cloud mining services allow users to rent a computer system and use that computer’s hash power to mine cryptocurrencies without having to manage the mining hardware themselves.
But according to Chainalysis, it’s not just nation-state hacking crews who are leveraging such services in the wild.
In one example highlighted by the company, mining pools and wallets associated with ransomware actors have been used to send funds to a “highly active deposit address” at an unnamed mainstream crypto exchange.
This includes $19.1 million from four ransomware wallet addresses and $14.1 million from three mining pools, with a significant chunk of the funds routed via a network of intermediary wallets and pools.
“In this scenario, the mining pool acts similarly to a mixer in that it obfuscates the origin of funds and creates the illusion that the funds are proceeds from mining rather than from ransomware,” Chainalysis noted.
In a sign that the trend is gaining traction, the cumulative value of assets sent from ransomware wallets to exchanges through mining pools has surged from less than $10,000 in Q1 2018 to almost $50 million in Q1 2023.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
That’s not all. As many as 372 exchange deposit addresses have been found to receive at least $1 million worth of cryptocurrency from mining pools and any amount from ransomware addresses since January 2018.
“Overall, the data suggests that mining pools may play a key role in many ransomware actors’ money laundering strategy,” Chainalysis said.
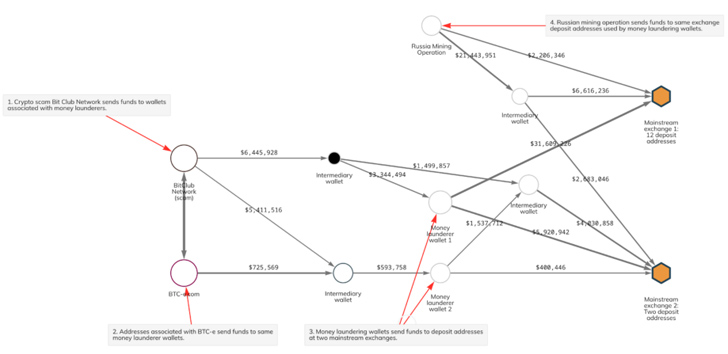
Mining pools have also earned a place in the playbooks of scam operators like the BitClub Network, who have been found commingling their illicit Bitcoin proceeds with assets received from a Russia-based Bitcoin mining operation and BTC-e, a crypto exchange that was set up to facilitate the laundering of money stolen in the infamous Mt. Gox hack.
“Crypto scammers and money launderers working on their behalf are also using mining pools as part of their money laundering process,” the company said. “Deposit addresses [with receipts of at least $1 million worth of crypto from mining pools] have received just under $1.1 billion worth of cryptocurrency from scam-related addresses since 2018.”
[ad_2]
Source link