[ad_1]
Microsoft on Friday disclosed that it has addressed a critical security flaw impacting Power Platform, but not before it came under criticism for its failure to swiftly act on it.
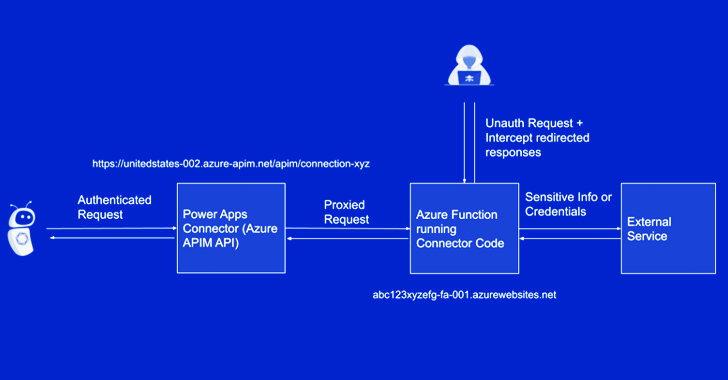
“The vulnerability could lead to unauthorized access to Custom Code functions used for Power Platform custom connectors,” the tech giant said. “The potential impact could be unintended information disclosure if secrets or other sensitive information were embedded in the Custom Code function.”
The company further noted that no customer action is required and that it found no evidence of active exploitation of the vulnerability in the wild.
Tenable, which initially discovered and reported the shortcoming to Redmond on March 30, 2023, said the problem could enable limited, unauthorized access to cross-tenant applications and sensitive data.

The cybersecurity firm said the flaw arises as a result of insufficient access control to Azure Function hosts, leading to a scenario where a threat actor could intercept OAuth client IDs and secrets, as well as other forms of authentication.
Microsoft is said to have issued an initial fix on June 7, 2023, but it wasn’t until August 2, 2023, that the vulnerability was completely plugged.
The months-long delay in patching the flaw attracted scrutiny from Tenable CEO Amit Yoran, who slammed the Windows maker for being “grossly irresponsible, if not blatantly negligent.”
“Cloud providers have long espoused the shared responsibility model,” Yoran said in a post shared on LinkedIn. “That model is irretrievably broken if your cloud vendor doesn’t notify you of issues as they arise and apply fixes openly.”

“What you hear from Microsoft is ‘just trust us,’ but what you get back is very little transparency and a culture of toxic obfuscation.”
The tech giant, in its own alert, said it follows an extensive process of investigating and deploying fixes and that “developing a security update is a delicate balance between speed and safety of applying the fix and quality of the fix.”
“Not all fixes are equal,” it further added. “Some can be completed and safely applied very quickly, others can take longer. In order to protect our customers from an exploit of an embargoed security vulnerability, we also start to monitor any reported security vulnerability of active exploitation and move swiftly if we see any active exploit.”
[ad_2]
Source link