[ad_1]
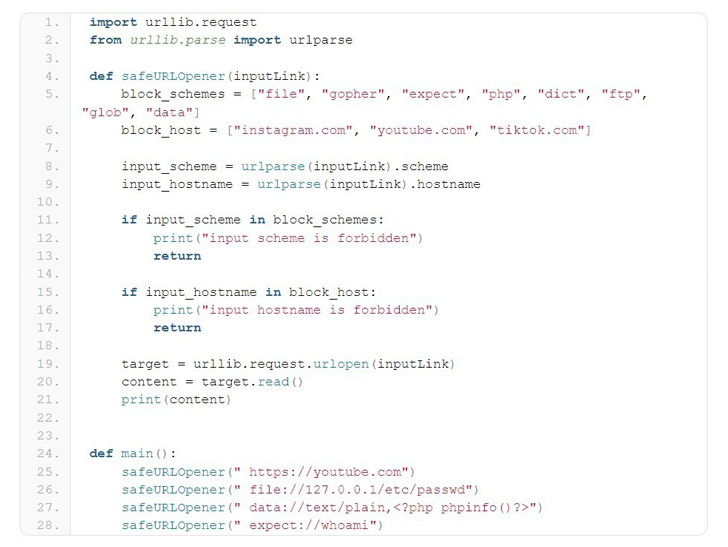
A high-severity security flaw has been disclosed in the Python URL parsing function that could be exploited to bypass domain or protocol filtering methods implemented with a blocklist, ultimately resulting in arbitrary file reads and command execution.
“urlparse has a parsing problem when the entire URL starts with blank characters,” the CERT Coordination Center (CERT/CC) said in a Friday advisory. “This problem affects both the parsing of hostname and scheme, and eventually causes any blocklisting methods to fail.”
The flaw has been assigned the identifier CVE-2023-24329 and carries a CVSS score of 7.5. Security researcher Yebo Cao has been credited with discovering and reporting the issue in August 2022. It has been addressed in the following versions –
- >= 3.12
- 3.11.x >= 3.11.4
- 3.10.x >= 3.10.12
- 3.9.x >= 3.9.17
- 3.8.x >= 3.8.17, and
- 3.7.x >= 3.7.17
urllib.parse is a widely used parsing function that makes it possible to break down URLs to its constituents, or alternatively, combine the components to a URL string.

CVE-2023-24329 arises as a result of a lack of input validation, thereby leading to a scenario where it’s possible to get around blocklisting methods by supplying a URL that starts with blank characters (e.g., ” https://youtube[.]com”).
“Although blocklist is considered an inferior choice, there are many scenarios where blocklist is still needed,” Cao said. “This vulnerability would help an attacker to bypass the protections set by the developer for scheme and host. This vulnerability can be expected to help SSRF and RCE in a wide range of scenarios.”
[ad_2]
Source link