[ad_1]
BlackLotus, the first in-the-wild malware to bypass Microsoft’s Secure Boot (even on fully patched systems), will spawn copycats and, available in an easy-to-use bootkit on the Dark Web, inspire firmware attackers to increase their activity, security experts said this week.
That means that companies need to increase efforts to validate the integrity of their servers, laptops, and workstations, starting now.
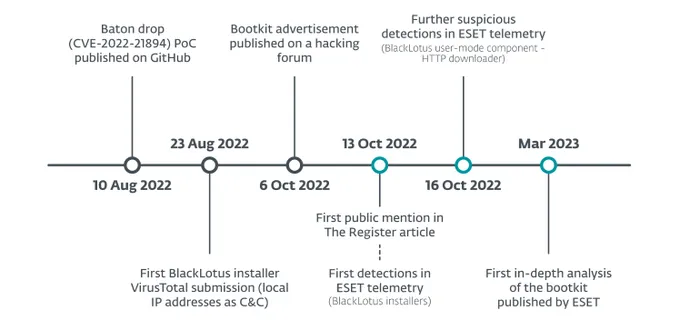
On March 1, cybersecurity firm ESET published an analysis of the BlackLotus bootkit, which bypasses a fundamental Windows security feature known as Unified Extensible Firmware Interface (UEFI) Secure Boot. Microsoft introduced Secure Boot more than a decade ago, and it’s now considered one of the foundations of its Zero Trust framework for Windows because of the difficulty in subverting it.
Yet threat actors and security researchers have targeted Secure Boot implementations more and more, and for good reason: Because UEFI is the lowest level of firmware on a system (responsible for the booting-up process), finding a vulnerability in the interface code allows an attacker to execute malware before the operating system kernel, security apps, and any other software can swing into action. This ensures the implantation of persistent malware that normal security agents will not detect. It also offers the ability to execute in kernel mode, to control and subvert every other program on the machine — even after OS reinstalls and hard drive replacements — and load additional malware at the kernel level.
There have been some previous vulnerabilities in boot technology, such as the BootHole flaw disclosed in 2020 that affected the Linux bootloader GRUB2, and a firmware flaw in five Acer laptop models that could be used to disable Secure Boot. The US Department of Homeland Security and Department of Commerce even recently warned about the persistent threat posed by firmware rootkits and bootkits in a draft report on supply chain security issues. But BlackLotus ups the stakes on firmware issues significantly.
That’s because while Microsoft patched the flaw that BlackLotus targets (a vulnerability known as Baton Drop or CVE-2022-21894), the patch only makes exploitation more difficult — not impossible. And the impact of the vulnerability will hard to measure, because affected users will likely not see signs of compromise, according to a warning from Eclypsium published this week.
“If an attacker does manage to get a foothold, companies could be running blind, because a successful attack means that an attacker is getting around all of your traditional security defenses,” says Paul Asadoorian, principal security evangelist at Eclypsium. “They can turn off logging, and essentially lie to every kind of defensive countermeasure you might have on the system to tell you that everything is okay.”
Now that BlackLotus has been commercialized, it paves the way for the development of similar wares, researchers note. “We expect to see more threat groups incorporating secure boot bypasses into their arsenal in the future,” says Martin Smolár, malware researcher at ESET. “Every threat actor’s ultimate goal is persistence on the system, and with UEFI persistence, they can operate much stealthier than with any other kind of OS-level persistence.”
Patching Is Not Enough
Even though Microsoft patched Baton Drop more than a year ago, the certificate of the vulnerable version remains valid, according to Eclypsium. Attackers with access to a compromised system can install a vulnerable bootloader and then exploit the vulnerability, gaining persistence and a more privileged level of control.
Microsoft maintains a list of cryptographic hashes of legitimate Secure Boot bootloaders. To prevent the vulnerable boot loader from working, the company would have to revoke the hash, but that would also prevent legitimate — although unpatched — systems from working.
“To fix this you have to revoke the hashes of that software to tell Secure Boot and Microsoft’s own internal process that that software is no longer valid in the boot process,” Asadoorian says. “They would have to issue the revocation, update the revocation list, but they’re not doing that, because it would break a lot of things.”
The best that companies can do is update their firmware and revocation lists on a regular basis, and monitor endpoints for indications that an attacker has made modifications, Eclypsium said in its advisory.
ESET’s Smolár, who led the earlier investigation into BlackLotus, said in a March 1 statement to expect exploitation to ramp up.
“The low number of BlackLotus samples we have been able to obtain, both from public sources and our telemetry, leads us to believe that not many threat actors have started using it yet,” he said. “We are concerned that things will change rapidly should this bootkit get into the hands of crimeware groups, based on the bootkit’s easy deployment and crimeware groups’ capabilities for spreading malware using their botnets.”
[ad_2]
Source link
