[ad_1]
A new malspam campaign has been observed deploying an off-the-shelf malware called DarkGate.
“The current spike in DarkGate malware activity is plausible given the fact that the developer of the malware has recently started to rent out the malware to a limited number of affiliates,” Telekom Security said in a report published last week.
The latest report build onn recent findings from security researcher Igal Lytzki, who detailed a “high volume campaign” that leverages hijacked email threads to trick recipients into downloading the malware.

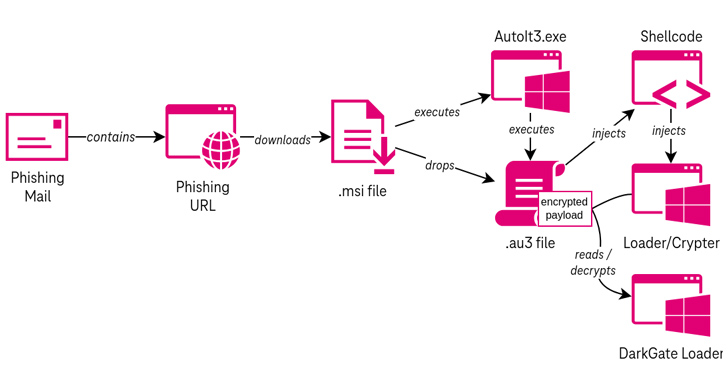
The attack commences with a phishing URL that, when clicked, passes through a traffic direction system (TDS) to take the victim to an MSI payload subject to certain conditions. This includes the presence of a refresh header in the HTTP response.
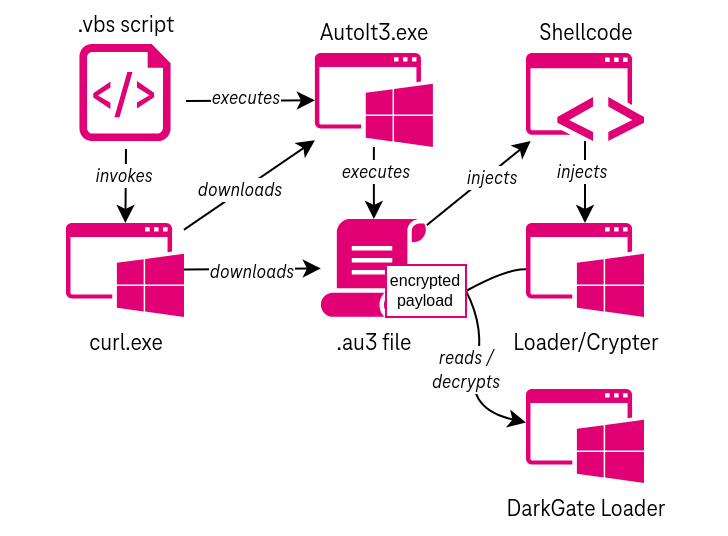
Opening the MSI file triggers a multi-stage process that incorporates an AutoIt script to execute shellcode that acts as a conduit to decrypt and launch DarkGate via a crypter (or loader).
Specifically, the loader is designed to parse the AutoIt script and extract the encrypted malware sample.
An alternate variation of the attacks have been observed using a Visual Basic Script in place of an MSI file, which, in turn, uses cURL to retrieve the AutoIt executable and script file. The exact method by which the VB Script is delivered is currently unknown.
DarkGate, sold mainly on underground forums by an actor named RastaFarEye, comes with capabilities to evade detection by security software, set up persistence using Windows Registry changes, escalate privileges, and steal data from web browsers and other software such as Discord and FileZilla.
It also establishes contact with a command-and-control (C2) server for enumerating files, data exfiltration, launching cryptocurrency miners, and remotely capturing screenshots as well as running other commands.

The malware is offered as a subscription that starts from $1,000 per day to $15,000 per month to $100,000 a year, with the author advertising it as the “ultimate tool for pentesters/redteamers” and that it has “features that you won’t find anywhere.” Interestingly, earlier versions of DarkGate also came fitted with a ransomware module.
Phishing attacks are a primary delivery pathway for stealers, trojans, and malware loaders such as KrakenKeylogger, QakBot, Raccoon Stealer, SmokeLoader, and others, with threat actors continuously adding new features and enhancements to expand their functionalities.
According to a recent report published by HP Wolf Security, email remained the top vector for delivering malware to endpoints, accounting for 79% of threats identified in Q2 2023.
[ad_2]
Source link