[ad_1]
Suspected North Korean nation-state actors targeted a journalist in South Korea with a malware-laced Android app as part of a social engineering campaign.
The findings come from South Korea-based non-profit Interlab, which coined the new malware RambleOn.
The malicious functionalities include the “ability to read and leak target’s contact list, SMS, voice call content, location and others from the time of compromise on the target,” Interlab threat researcher Ovi Liber said in a report published this week.
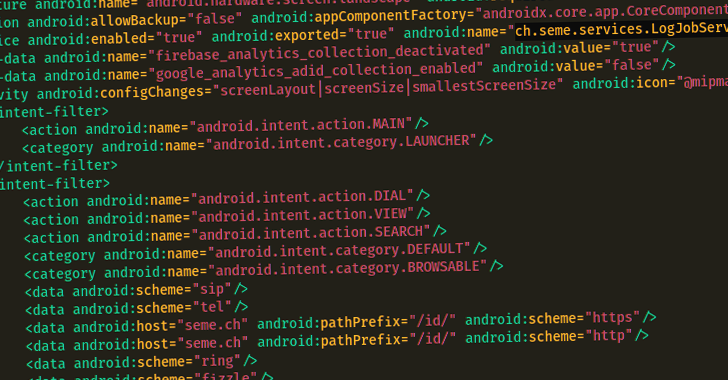
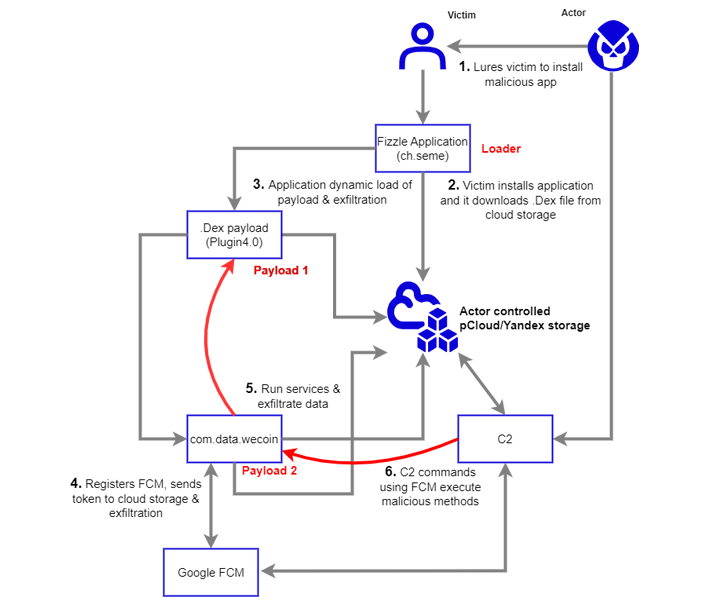
The spyware camouflages as a secure chat app called Fizzle (ch.seme), but in reality, acts as a conduit to deliver a next-stage payload hosted on pCloud and Yandex.
The chat app is said to have been sent as an Android Package (APK) file over WeChat to the targeted journalist on December 7, 2022, under the pretext of wanting to discuss a sensitive topic.
The primary purpose of RambleOn is to function as a loader for another APK file (com.data.WeCoin) while also requesting for intrusive permissions to collect files, access call logs, intercept SMS messages, record audio, and location data.
The secondary payload, for its part, is designed to provide an alternative channel for accessing the infected Android device using Firebase Cloud Messaging (FCM) as a command-and-control (C2) mechanism.
Interlab said it identified overlaps in the FCM functionality between RambleOn and FastFire, a piece of Android spyware that was attributed to Kimsuky by South Korean cybersecurity company S2W last year.
“The victimology of this event fits very closely with the modus operandi of groups such as APT37 and Kimsuky,” Liber said, pointing out the former’s use of pCloud and Yandex storage for payload delivery and command-and-control.
[ad_2]
Source link