[ad_1]
GitHub on Thursday announced that it’s enabling secret scanning push protection by default for all pushes to public repositories.
“This means that when a supported secret is detected in any push to a public repository, you will have the option to remove the secret from your commits or, if you deem the secret safe, bypass the block,” Eric Tooley and Courtney Claessens said.
Push protection was first piloted as an opt-in feature in August 2023, although it has been under testing since April 2022. It became generally available in May 2023.
The secret scanning feature is designed to identify over 200 token types and patterns from more than 180 service providers in order to prevent their fraudulent use by malicious actors.
The development comes nearly five months after the Microsoft subsidiary expanded secret scanning to include validity checks for popular services such as Amazon Web Services (AWS), Microsoft, Google, and Slack.
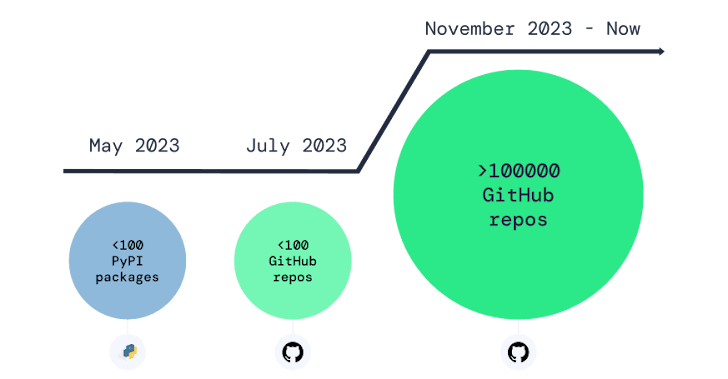
It also follows the discovery of an ongoing “repo confusion” attack targeting GitHub that’s inundating the source code hosting platform with thousands of repositories containing obfuscated malware capable of stealing passwords and cryptocurrency from developer devices.
The attacks represent another wave of the same malware distribution campaign that was disclosed by Phylum and Trend Micro last year, leveraging bogus Python packages hosted on the cloned, trojanized repositories to deliver a stealer malware called BlackCap Grabber.
“Repo confusion attacks simply rely on humans to mistakenly pick the malicious version over the real one, sometimes employing social engineering techniques as well,” Apiiro said in a report this week.
[ad_2]
Source link