[ad_1]
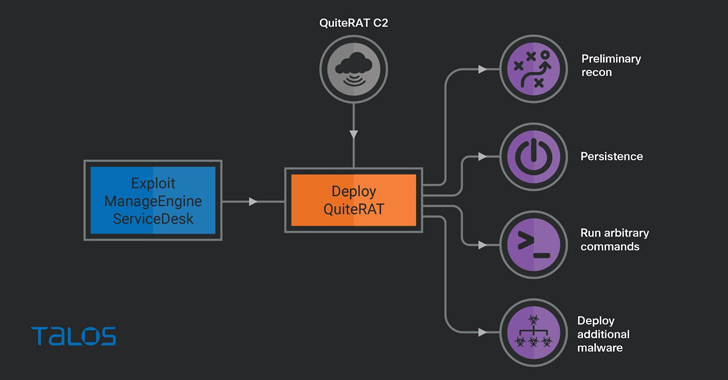
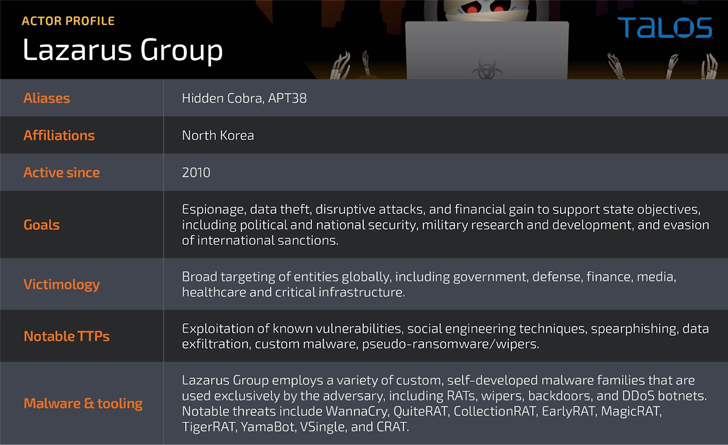
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT.
Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S., cybersecurity company Cisco Talos said in a two-part analysis published today.
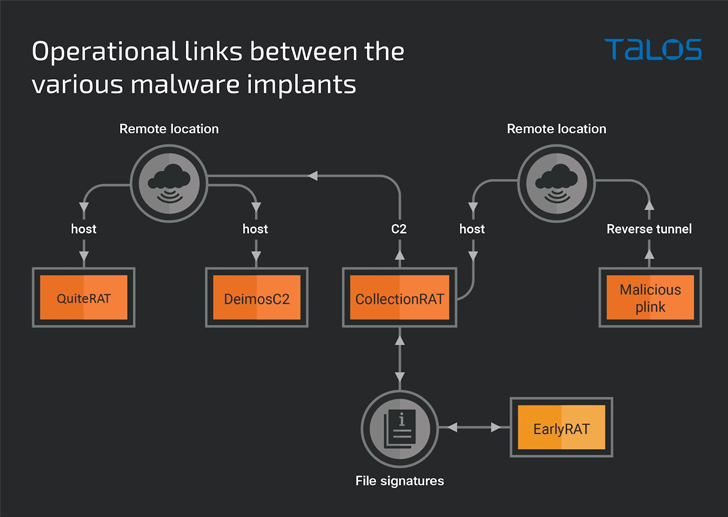
What’s more, a closer examination of the adversary’s recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT.
The fact that the Lazarus Group continues to rely on the same tradecraft despite those components being well-documented over the years underscores the threat actor’s confidence in their operations, Talos pointed out.
QuiteRAT is said to be a successor to MagicRAT, itself a follow-up to TigerRAT, while CollectionRAT appears to share overlaps with EarlyRAT (aka Jupiter), an implant written in PureBasic with capabilities to run commands on the endpoint.

“QuiteRAT has many of the same capabilities as Lazarus Group’s better-known MagicRAT malware, but its file size is significantly smaller,” security researchers Asheer Malhotra, Vitor Ventura, and Jungsoo An said. “Both implants are built on the Qt framework and include capabilities such as arbitrary command execution.”
The use of the Qt framework is seen as an intentional effort on the part of the adversary to make analysis a lot more challenging as it “increases the complexity of the malware’s code.”
The activity, detected in early 2023, involved the exploitation of CVE-2022-47966, a mere five days after proof-of-concept (Poc) for the flaw emerged online, to directly deploy the QuiteRAT binary from a malicious URL.
“QuiteRAT is clearly an evolution of MagicRAT,” the researchers said. “While MagicRAT is a bigger, bulkier malware family averaging around 18 MB in size, QuiteRAT is a much much smaller implementation, averaging around 4 to 5 MB in size.”
Another crucial difference between the two is the lack of a built-in persistence mechanism in QuiteRAT, necessitating that a command be issued from the server to ensure continued operation on the compromised host.
The findings also overlap with another campaign uncovered by WithSecure earlier this February in which security flaws in unpatched Zimbra devices were used to breach victim systems and ultimately install QuiteRAT.

Cisco Talos said the adversary is “increasingly relying on open-source tools and frameworks in the initial access phase of their attacks, as opposed to strictly employing them in the post-compromise phase.”
This includes the GoLang-based open-source DeimosC2 framework to obtain persistent access, with CollectionRAT primarily utilized to gather metadata, run arbitrary commands, manage files on the infected system, and deliver additional payloads.
It’s not immediately clear how CollectionRAT is propagated, but evidence shows that a trojanized copy of the PuTTY Link (Plink) utility hosted on the same infrastructure is being used to establish a remote tunnel to the system and serve the malware.
“Lazarus Group previously relied on the use of custom-built implants such as MagicRAT, VSingle, Dtrack, and YamaBot as a means of establishing persistent initial access on a successfully compromised system,” the researchers said.
“These implants are then instrumented to deploy a variety of open-source or dual-use tools to perform a multitude of malicious hands-on-keyboard activities in the compromised enterprise network.”
The development is a sign that the Lazarus Group is continually shifting tactics and expanding its malicious arsenal, at the same time weaponizing newly disclosed vulnerabilities in software to devastating effect.
[ad_2]
Source link