[ad_1]
Threat actors are leveraging a technique called versioning to evade Google Play Store’s malware detections and target Android users.
“Campaigns using versioning commonly target users’ credentials, data, and finances,” Google Cybersecurity Action Team (GCAT) said in its August 2023 Threat Horizons Report shared with The Hacker News.
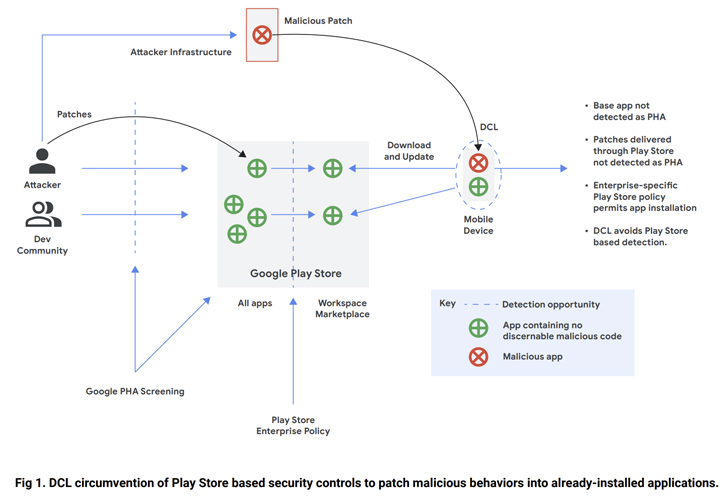
While versioning is not a new phenomenon, it’s sneaky and hard to detect. In this method, a developer releases an initial version of an app on the Play Store that passes Google’s pre-publication checks, but is later updated with a malware component.
This is achieved by pushing an update from an attacker-controlled server to serve malicious code on the end user device using a method called dynamic code loading (DCL), effectively turning the app into a backdoor.

Earlier this May, ESET discovered a screen recording app named “iRecorder – Screen Recorder” that remained innocuous for nearly a year after it was first uploaded to the Play Store before malicious changes were introduced sneakily to spy on its users.
Another example of malware using the DCL method is SharkBot, which has repeatedly made an appearance on the Play Store by masquerading as security and utility apps.
SharkBot is a financial trojan that initiates unauthorized money transfers from compromised devices using the Automated Transfer Service (ATS) protocol.
Dropper applications that appear on the storefront come with reduced functionality that, once installed by the victims, download a full version of the malware in a bid to attract less attention.
“In an enterprise environment, versioning demonstrates a need for defense-in-depth principles, including but not limited to limiting application installation sources to trusted sources such as Google Play or managing corporate devices via a mobile device management (MDM) platform,” the company said.
The findings come as ThreatFabric revealed that malware purveyors have been exploiting a bug in Android to pass off malicious apps as benign by “corrupting components of an app” such that the app as a whole remains valid, according to KrebsOnSecurity.

“Actors can have several apps published in the store at the same time under different developer accounts, however, only one is acting as malicious, while the other is a backup to be used after takedown,” the Dutch cybersecurity company noted in June.
“Such a tactic helps actors to maintain very long campaigns, minimizing the time needed to publish another dropper and continue the distribution campaign.”
To mitigate any potential risks, it’s recommended that Android users stick to trusted sources for downloading apps and enable Google Play Protect to receive notifications when a potentially harmful app (PHA) is found on the device.
[ad_2]
Source link