[ad_1]
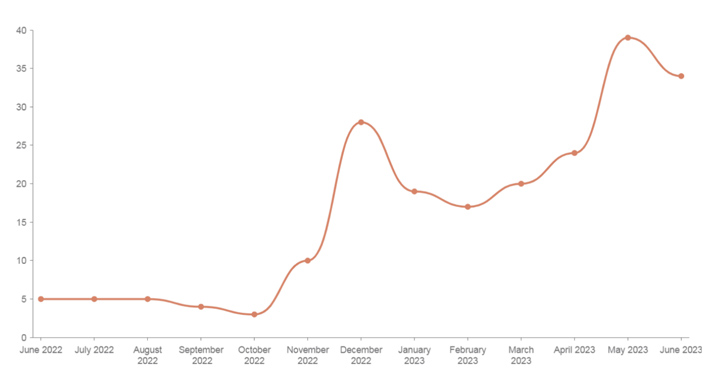
Mallox ransomware activities in 2023 have witnessed a 174% increase when compared to the previous year, new findings from Palo Alto Networks Unit 42 reveal.
“Mallox ransomware, like many other ransomware threat actors, follows the double extortion trend: stealing data before encrypting an organization’s files, and then threatening to publish the stolen data on a leak site as leverage to convince victims to pay the ransom fee,” security researchers Lior Rochberger and Shimi Cohen said in a new report shared with The Hacker News.
Mallox is linked to a threat actor that’s also linked to other ransomware strains, such as TargetCompany, Tohnichi, Fargo, and, most recently, Xollam. It first burst onto the scene in June 2021.
Some of the prominent sectors targeted by Mallox are manufacturing, professional and legal services, and wholesale and retail.
A notable aspect of the group is its pattern of exploiting poorly secured MS-SQL servers via dictionary attacks as a penetration vector to compromise victims’ networks. Xollam is a deviation from the norm in that it has been observed using malicious OneNote file attachments for initial access, as detailed by Trend Micro last month.
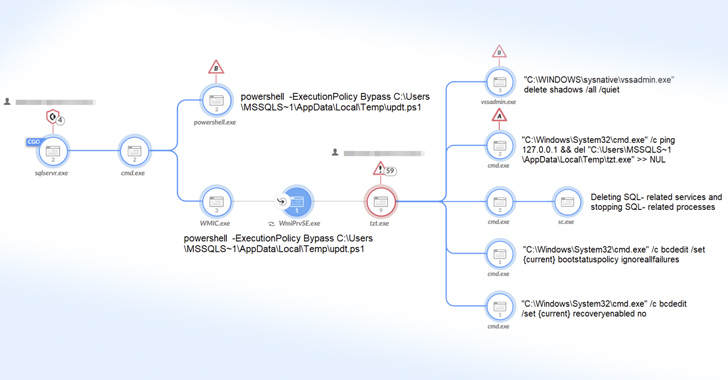
Upon gaining a successful foothold on the infected host, a PowerShell command is executed to retrieve the ransomware payload from a remote server.
The binary, for its part, attempts to stop and remove SQL-related services, delete volume shadow copies, clear system event logs, terminate security-related processes, and bypass Raccine, an open-source tool designed to counter ransomware attacks, prior to commencing its encryption process, after which a ransom note is dropped in every directory.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
TargetCompany remains a small, closed group, but it has also been observed recruiting affiliates for the Mallox ransomware-as-a-service (RaaS) affiliate program on the RAMP cybercrime forum.
The development comes as ransomware continues to be a lucrative financial scheme, netting cybercriminals no less than $449.1 million in the first half of 2023 alone, per Chainalysis.
“The Mallox ransomware group has been more active in the past few months, and their recent recruiting efforts may enable them to attack more organizations if the recruitment drive is successful,” the researchers said.
[ad_2]
Source link