[ad_1]
Researchers have pulled back the curtain on an updated version of an Apple macOS malware called Rustbucket that comes with improved capabilities to establish persistence and avoid detection by security software.
“This variant of Rustbucket, a malware family that targets macOS systems, adds persistence capabilities not previously observed,” Elastic Security Labs researchers said in a report published this week, adding it’s “leveraging a dynamic network infrastructure methodology for command-and-control.”
RustBucket is the work of a North Korean threat actor known as BlueNoroff, which is part of a larger intrusion set tracked under the name Lazarus Group, an elite hacking unit supervised by the Reconnaissance General Bureau (RGB), the country’s primary intelligence agency.
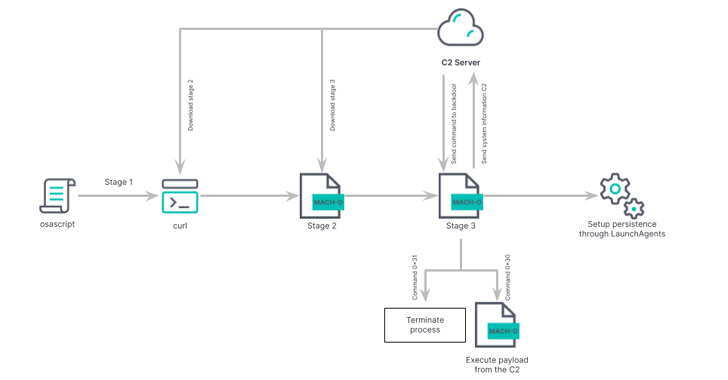
The malware came to light in April 2023, when Jamf Threat Labs described it as an AppleScript-based backdoor capable of retrieving a second-stage payload from a remote server. Elastic is monitoring the activity as REF9135.
The second-stage malware, compiled in Swift, is designed to download from the command-and-control (C2) server the main malware, a Rust-based binary with features to gather extensive information as well as fetch and run additional Mach-O binaries or shell scripts on the compromised system.
It’s the first instance of BlueNoroff malware specifically targeting macOS users, although a .NET version of RustBucket has since surfaced in the wild with a similar set of features.
“This recent Bluenoroff activity illustrates how intrusion sets turn to cross-platform language in their malware development efforts, further expanding their capabilities highly likely to broaden their victimology,” French cybersecurity company Sekoia said in an analysis of the RustBucket campaign in late May 2023.
The infection chain consists of a macOS installer file that installs a backdoored, yet functional, PDF reader. A significant aspect of the attacks is that the malicious activity is triggered only when a weaponized PDF file is launched using the rogue PDF reader. Initial intrusion vector includes phishing emails, as well as employing bogus personas on social networks such as LinkedIn.
The observed attacks are highly targeted and focused on finance-related institutions in Asia, Europe, and the U.S., suggesting that the activity is geared towards illicit revenue generation to evade sanctions.
What makes the newly identified version notable is its unusual persistence mechanism and the use of dynamic DNS domain (docsend.linkpc[.]net) for command-and-control, alongside incorporating measures focused on remaining under the radar.
“In the case of this updated RUSTBUCKET sample, it establishes its own persistence by adding a plist file at the path /Users/<user>/Library/LaunchAgents/com.apple.systemupdate.plist, and it copies the malware’s binary to the following path /Users/<user>/Library/Metadata/System Update,” the researchers said.
[ad_2]
Source link