[ad_1]
The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group’s features and tactics.
APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea’s Ministry of State Security (MSS) unlike the Lazarus and Kimsuky threat clusters that are part of the Reconnaissance General Bureau (RGB).
According to Google-owned Mandiant, MSS is tasked with “domestic counterespionage and overseas counterintelligence activities,” with APT37’s attack campaigns reflective of the agency’s priorities. The operations have historically singled out individuals such as defectors and human rights activists.
“APT37’s assessed primary mission is covert intelligence gathering in support of DPRK’s strategic military, political, and economic interests,” the threat intelligence firm said.
The threat actor is known to rely on customized tools such as Chinotto, RokRat, BLUELIGHT, GOLDBACKDOOR, and Dolphin to harvest sensitive information from compromised hosts.
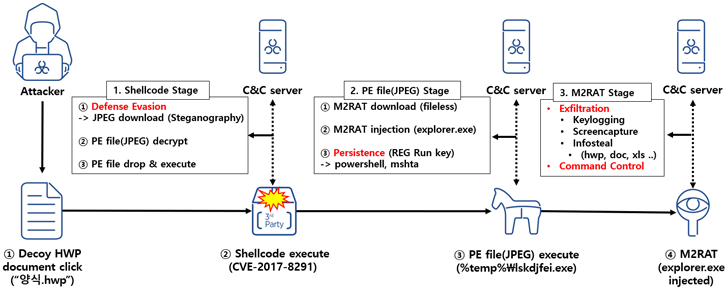
“The main feature of this RedEyes Group attack case is that it used a Hangul EPS vulnerability and used steganography techniques to distribute malicious codes,” AhnLab Security Emergency response Center (ASEC) said in a report published Tuesday.
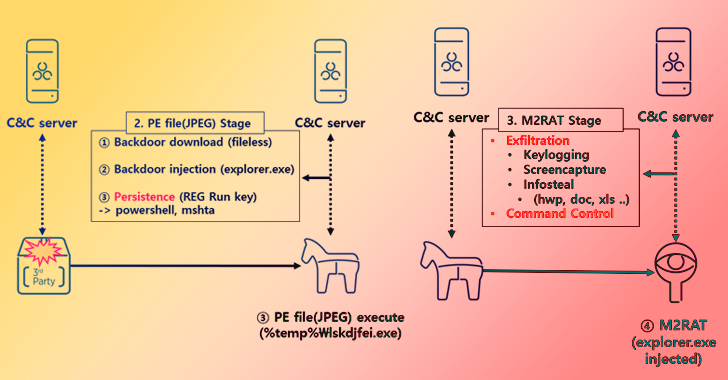
The infection chain observed in January 2023 commences with a decoy Hangul document, which exploits a now-patched flaw in the word processing software (CVE-2017-8291) to trigger shellcode that downloads an image from a remote server.
The JPEG file uses steganographic techniques to conceal a portable executable that, when launched, downloads the M2RAT implant and injects it into the legitimate explorer.exe process.
While persistence is achieved by means of a Windows Registry modification, M2RAT functions as a backdoor capable of keylogging, screen capture, process execution, and information theft. Like Dolphin, it’s also designed to siphon data from removable disks and connected smartphones.
“These APT attacks are very difficult to defend against, and the RedEyes group in particular is known to primarily target individuals, so it can be difficult for non-corporate individuals to even recognize the damage,” ASEC said.
This is not the first time CVE-2017-8291 has been weaponized by North Korean threat actors. In late 2017, the Lazarus Group was observed targeting South Korean cryptocurrency exchanges and users to deploy Destover malware, according to Recorded Future.
[ad_2]
Source link