[ad_1]
The discovery of moderate to severe vulnerabilities in the baseboard management controllers (BMCs) used by 15 different vendors highlighted the danger of firmware flaws in December 2022. Because firmware lives closer to the hardware level, where more most security scanners cannot reach, it’s difficult to find and address vulnerabilities. And because firmware components are so foundational and widely deployed, breaching one can give an attacker access to entire networks.
Bootkits and rootkits like BlackLotus, CosmicStrand, and MoonBounce have expanded the attack surface to the firmware level, despite firmware security measures in operating systems like Windows 11.
So the stakes and the challenges are high. “That’s precisely why Binarly was created,” says Alex Matrosov, founder and CEO of Binarly, a finalist in the Black Hat USA Startup Spotlight Competition this year. In short, Binarly created a binary analysis tool that finds known and unknown vulnerabilities in firmware. The technology also can assess the accuracy and thoroughness of software bills of materials (SBOMs) to identify linked dependencies.
Matrosov says, “We are building the Binarly Transparency Platform to address supply chain security at scale and help pinpoint signs of tampering and firmware implantation.”
How Binarly Gets Into the Firmware
“At Binarly, we believe in automation because people don’t scale well, and we are pioneering a new approach focused on modern AI/ML to find and mitigate attack surfaces below the operating system,” Matrosov says.
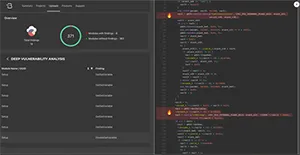
Like antivirus software has, firmware scanning is moving away from detecting known problems based on signatures and toward analyzing code to find previously unknown issues. Binarly implements machine learning that studies known vulnerability classes, finds portions of similar code, classifies the vulnerabilities thus discovered, and predicts and proves how exploitable those new vulnerabilities are. The figure shows Deep Vulnerability Analysis with reach explainability, which highlights vulnerable code snippets.
The company says this process can keep products from getting released with vulnerabilities, thus reducing the incident response impact on both Binarly clients and their downstream customers. Binarly also hosts FwHunt, which allows developers to upload their firmware to scan it with the company’s tools.
“We have ambitious plans to further enhance the platform’s capability to identify various classes of issues and expedite the process of identifying and resolving identified vulnerabilities,” Matrosov says. He adds that his company used its platform to identify and disclose more than 320 high-impact vulnerabilities last year.
“In the past quarter, we’ve been focusing on productizing some research we have been doing to enable us to go beyond just finding issues and moving to help security professionals and developers understand how those issues work and how to fix them,” Matrosov says.
Firm Grip on the Future
The four finalists in the Black Hat Startup Spotlight — Binarly, Mobb, Endor Labs, and Gomboc — will present their business models to a panel of judges at the Mandalay Bay in Las Vegas on Wednesday, Aug. 9. Dark Reading’s editor-in-chief, Kelly Jackson Higgins, will host the event, which begins at 4:30 p.m. PT.
Binarly also promises swag and demos of the vulnerabilities the company has uncovered. In addition, Matrosov will sign copies of his book, Rootkits and Bootkits: Reversing Modern Malware and Next Generation Threats, written with Intel senior security researcher Eugene Rodionov and DARPA Information Innovation Office program manager Sergey Bratus.
The company name is not an adverb, as the -ly ending might suggest. Instead, it springs from Matrosov’s love of surfing. Binarly combines “binary analysis” and the surfing term “gnarly,” which refers to large, difficult, and dangerous waves — so the company addresses “bi-gnarly” problems.
Speed Round
Website: https://binarly.io/
Founded: April 13, 2021
Funding stage: Seed
Total funding raised so far: $3.6M
Number of employees: 16
If the company were a band, what would its band name be, and what kind of band would it be: Bad Devices (Punk Rock)
Pineapple on pizza, yea or nay?: “Pineapple on pizza is actually great if you do it right, so yea.”
[ad_2]
Source link