[ad_1]
Threat actors have been observed serving malicious code by utilizing Binance’s Smart Chain (BSC) contracts in what has been described as the “next level of bulletproof hosting.”
The campaign, detected two months ago, has been codenamed EtherHiding by Guardio Labs.
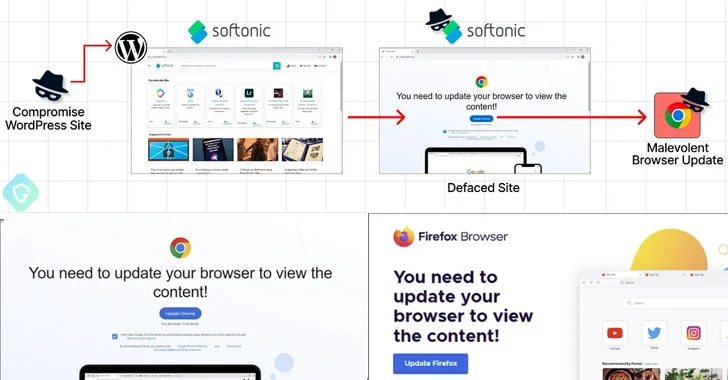
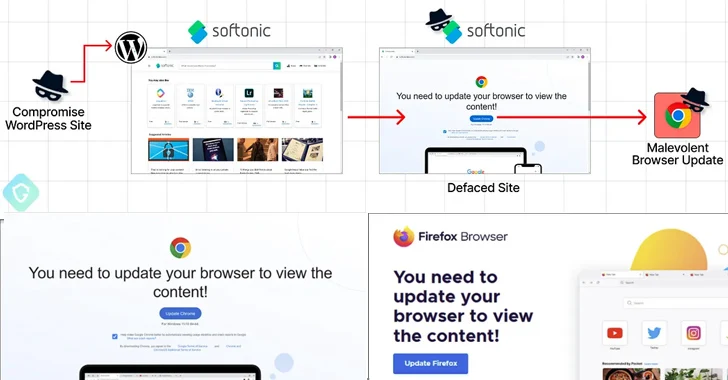
The novel twist marks the latest iteration in an ongoing campaign that leverages compromised WordPress sites to serve unsuspecting visitors a fake warning to update their browsers before the sites can be accessed, ultimately leading to the deployment of information stealer malware such as Amadey, Lumma, or RedLine.
“While their initial method of hosting code on abused Cloudflare Worker hosts was taken down, they’ve quickly pivoted to take advantage of the decentralized, anonymous, and public nature of blockchain,” security researchers Nati Tal and Oleg Zaytsev said.
“This campaign is up and harder than ever to detect and take down.”
It’s no surprise that threat actors have targeted WordPress sites via both malicious plugins, as well as take advantage of publicly disclosed security flaws in popular plugins to breach websites. This gives the ability to completely hijack infected websites at will.
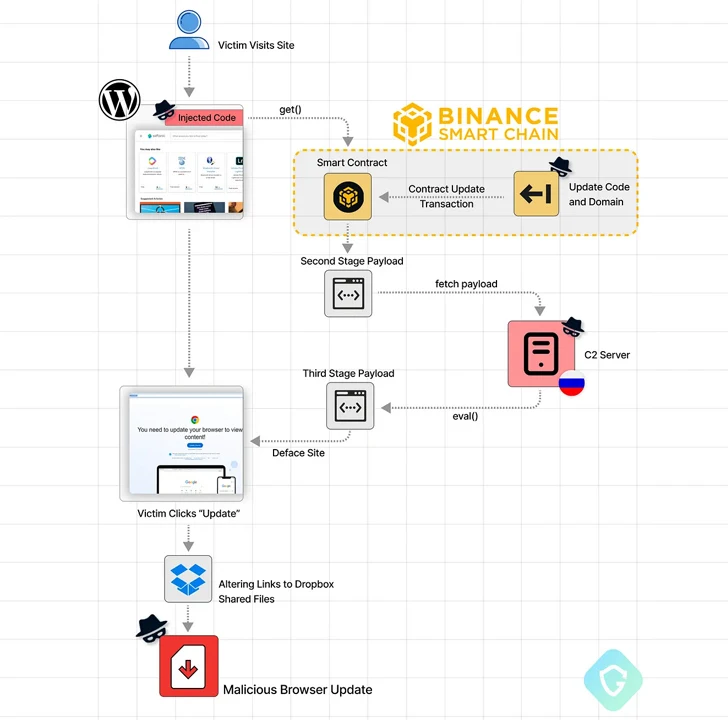
In the latest set of attacks, the infected sites are injected with obfuscated Javascript designed to query the BNB Smart Chain by creating a smart contract with an attacker-controlled blockchain address.
The goal is to fetch a second-stage script that, in turn, retrieves a third-stage payload from a command-and-control (C2) server to serve the deceptive browser update notices.
Should a victim click the update button on the bogus overlay, they are redirected to download a malicious executable from Dropbox or other legitimate file hosting services.
While the address and the associated contract have been tagged as used in a phishing scheme, the consequence of hosting it on a decentralized service means that there is currently no way to intervene and disrupt the attack chain.
“As this is not an address used in any financial or other activity that victims can be lured to transfer funds or any other kind of Intellectual property to — visitors of compromised WordPress sites have no clue as to what is going on under the hood,” the researchers explained.
“This contract, tagged as fake, malicious, or whatnot, is still online and delivers the malicious payload.”
With plugins becoming a sizable attack surface for WordPress, it’s recommended that users relying on the content management system (CMS) adhere to security best practices and keep their systems up-to-date with the latest patches, remove unwanted admin users, and enforce strong passwords.
[ad_2]
Source link