[ad_1]
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution (RCE) on vulnerable systems.
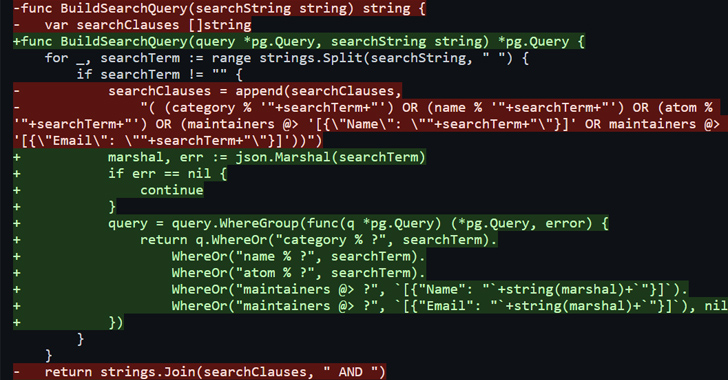
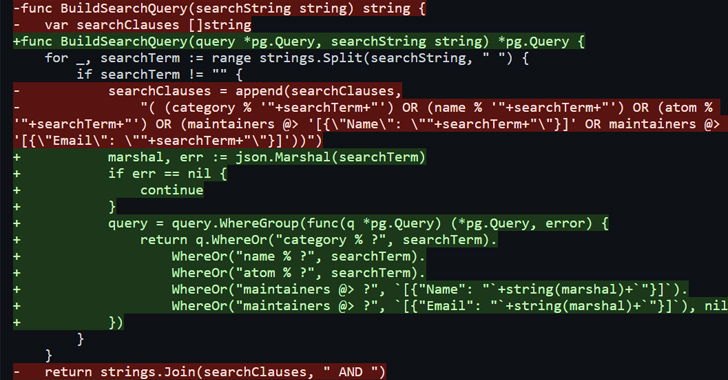
“These SQL injections happened despite the use of an Object-Relational Mapping (ORM) library and prepared statements,” SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a “misconfiguration of the database.”
The two issues, which were discovered in the search feature of Soko, have been collectively tracked as CVE-2023-28424 (CVSS score: 9.1). They were addressed within 24 hours of responsible disclosure on March 17, 2023.
Soko is a Go software module that powers packages.gentoo.org, offering users an easy way to search through different Portage packages that are available for Gentoo Linux distribution.
But the shortcomings identified in the service meant that it could have been possible for a malicious actor to inject specially crafted code, resulting in the exposure of sensitive information.
“The SQL injections were exploitable and had the ability to disclose the PostgreSQL server’s version and execute arbitrary commands on the system,” SonarSource said.
The development comes months after SonarSource uncovered a cross-site scripting (XSS) flaw in an open-source business suite called Odoo that could be exploited to impersonate any victim on a vulnerable Odoo instance as well as exfiltrate valuable data.
Earlier this year, security weaknesses were also disclosed in open-source software such as Pretalx and OpenEMR that could pave the way for remote attackers to execute arbitrary code.
[ad_2]
Source link