[ad_1]
An active financially motivated campaign is targeting vulnerable SSH servers to covertly ensnare them into a proxy network.
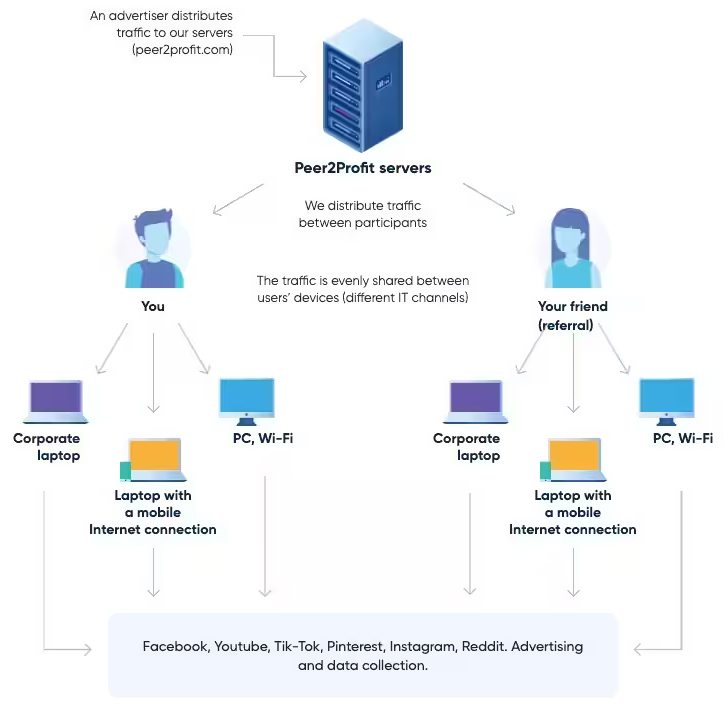
“This is an active campaign in which the attacker leverages SSH for remote access, running malicious scripts that stealthily enlist victim servers into a peer-to-peer (P2P) proxy network, such as Peer2Profit or Honeygain,” Akamai researcher Allen West said in a Thursday report.
Unlike cryptojacking, in which a compromised system’s resources are used to illicitly mine cryptocurrency, proxyjacking offers the ability for threat actors to leverage the victim’s unused bandwidth to clandestinely run different services as a P2P node.
This offers two-fold benefits: It not only enables the attacker to monetize the extra bandwidth with a significantly reduced resource load that would be necessary to carry out cryptojacking, it also reduces the chances of discovery.
“It is a stealthier alternative to cryptojacking and has serious implications that can increase the headaches that proxied Layer 7 attacks already serve,” West said.
To make matters worse, the anonymity provided by proxyware services can be a double-edged sword in that they could be abused by malicious actors to obfuscate the source of their attacks by routing traffic through intermediary nodes.
Akamai, which discovered the latest campaign on June 8, 2023, said the activity is designed to breach susceptible SSH servers and deploy an obfuscated Bash script that, in turn, is equipped to fetch necessary dependencies from a compromised web server, including the curl command-line tool by camouflaging it as a CSS file (“csdark.css”).
The stealthy script further actively searches for and terminates competing instances running bandwidth-sharing programs, before launching Docker services that share the victim’s bandwidth for profits.
A further examination of the web server has revealed that it’s also being used to host a cryptocurrency miner, suggesting that the threat actors are dabbling in both cryptojacking and proxyjacking attacks.
While proxyware is not inherently nefarious, Akamai noted that “some of these companies do not properly verify the sourcing of the IPs in the network, and even occasionally suggest that people install the software on their work computers.”
But such operations can also transcend into the realm of cybercrime when the applications are installed without the users’ knowledge or consent, thereby allowing the threat actor to control several systems and generate illegitimate revenue.
“Old techniques remain effective, especially when paired with new outcomes,” West said. “Standard security practices remain an effective prevention mechanism, including strong passwords, patch management, and meticulous logging.”
[ad_2]
Source link