[ad_1]
The most recent Gcore Radar report and its aftermath have highlighted a dramatic increase in DDoS attacks across multiple industries. At the beginning of 2023, the average strength of attacks reached 800 Gbps, but now, even a peak as high as 1.5+ Tbps is unsurprising. To try and break through Gcore’s defenses, perpetrators made two attempts with two different strategies. Read on to discover what happened and learn how the security provider stopped the attackers in their tracks without affecting end users’ experiences.
A Powerful DDoS Attacks
In November 2023, one of Gcore’s customers from the gaming industry was targeted by two massive DDoS attacks, peaking at 1.1 and 1.6 Tbps respectively. The attackers deployed various techniques in an unsuccessful attempt to compromise Gcore’s protective mechanisms.
Attack #1: 1.1 Tbps UDP-based DDoS
In the first cyber assault, the attackers sent a barrage of UDP traffic to a target server, peaking at 1.1 Tbps. Two methods were employed:
- By using random UDP source ports, they hoped to evade conventional filtering mechanisms.
- The attackers concealed their genuine identity by forging source IP addresses.
This was a classic flood (or volumetric) attack, whereby the attackers hoped to consume all available bandwidth of or to a data center or network, overwhelming the target servers with traffic and making them unavailable to legitimate users.
The graph below shows customer’s traffic during the attack. The peak of 1.1 Tbps shows an aggressive but short-lived attempt to flood the network with data. The green line (“total.general.input”) shows all inbound traffic. The other colored lines on the graph represent the network’s responses, including measures to filter and drop malicious traffic, as the system manages the deluge of data.
 |
| The attack comprised a short but intense peak of 1.1 Tbps around 22:55 |
Attack #2: 1.6 Tbps TCP-based DDoS
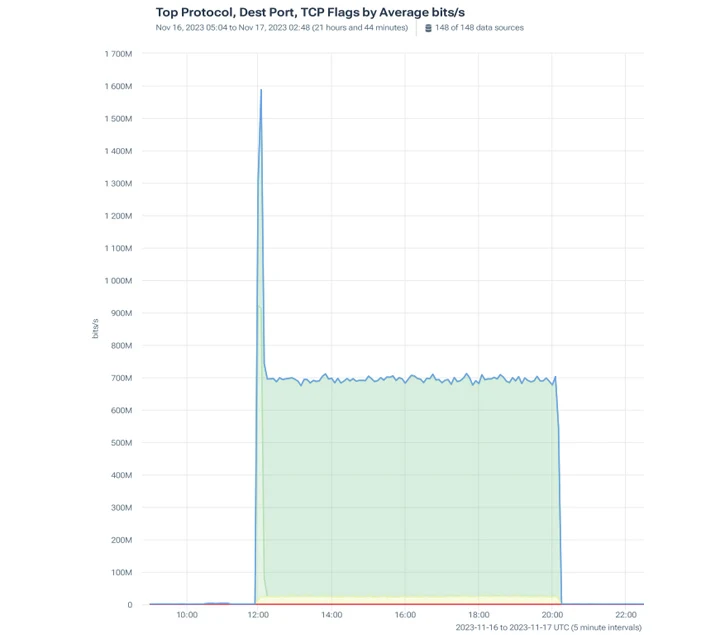 |
| The attack’s consistent traffic volume was 700 Mbps and at the onset peaked at 1600 Mbps |
This time, the attackers attempted to exploit TCP protocol with a mix of SYN flood, PSH, and ACK traffic.
In a SYN flood attack, several SYN packets are delivered to the target server without ACK packets. This means the server generates a half-open connection for each SYN packet. If successful, the server will ultimately run out of resources and stop accepting connections.
The PSH, ACK phase of the attack rapidly sends data to the target system. The ACK flag signals that the server received the previous packet. This pushes the system to handle data promptly, wasting resources. A SYN flood assault using PSH, ACK packets is harder to defend against than a SYN flood, since the PSH flag causes the server to process the packet contents immediately, consuming more resources.
As before, the goal was to overload the customer’s servers and make their services inaccessible to authorized users. This SYN flood had a peak volume of 685.77 Mbps and the PSH, ACK had a magnitude of 906.73 Mbps.
Gcore’s Defensive Strategies
Gcore’s DDoS Protection effectively neutralized both attacks while preserving regular service for the customer’s end users. The general approach of fending off DDoS security threats includes several techniques, such as Gcore’s front-line defenses:
- Dynamic traffic shaping: Dynamically adjusted traffic rates effectively mitigate the impact of the attack while ensuring the continuity of critical services. In order to prioritize genuine traffic while slowing harmful transmissions, adaptive thresholds and rate restrictions are used.
- Anomaly detection and quarantine: Models based on machine learning analyze behavior to identify anomalies. When an anomaly occurs, automated quarantine mechanisms redirect erroneous traffic to isolated segments for additional analysis.
- Regular expression filters: To block malicious payloads without disrupting legitimate traffic, regular expression-based filter rules are implemented. Their continuous fine-tuning ensures optimal protection without false positives.
- Collaborative threat intelligence: Gcore actively engages in the exchange of threat intelligence with industry peers. Collective insights and real-time threat feeds guide Gcore’s security techniques, allowing a rapid response to developing attack vectors.
By employing these strategies, Gcore was able to effectively mitigate the impact of DDoS attacks and protect their customer’s platform from disruption, negating potential reputational and financial losses.
Conclusion
DDoS attacks of 1.5+ Tbps volume pose an increasing danger across industries, with attackers using imaginative techniques to try and bypass protection services. Over the course of 2023, Gcore has registered increases in both average and maximum attack volumes, and these two connected attacks demonstrate that trend.
In the attacks covered in the article, Gcore was able to prevent any damage through a combination of dynamic traffic shaping, anomaly detection, regular expression filters, and collaborative threat intelligence. Explore DDoS Protection options to secure your network against ever-evolving DDoS threats.
[ad_2]
Source link

