[ad_1]
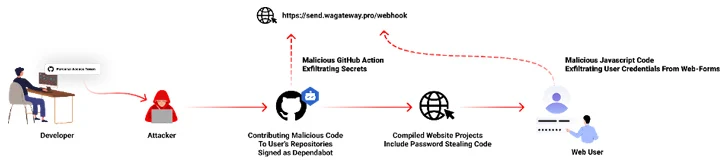
A new malicious campaign has been observed hijacking GitHub accounts and committing malicious code disguised as Dependabot contributions with an aim to steal passwords from developers.
“The malicious code exfiltrates the GitHub project’s defined secrets to a malicious C2 server and modify any existing javascript files in the attacked project with a web-form password-stealer malware code effecting any end-user submitting its password in a web form,” Checkmarx said in a technical report.
The malware is also designed to capture GitHub secrets and variables to a remote server by means of a GitHub Action.

The software supply chain security firm said it observed the atypical commits to hundreds of public and private GitHub repositories between July 8 and 11, 2023.
It has emerged that the victims had their GitHub personal access tokens stolen and used by the threat actors to make malicious code commits to users’ repositories by posing as Dependabot.
Dependabot is designed to alert users of security vulnerabilities in a project’s dependencies by automatically generating pull requests to keep them up-to-date.
“The attackers accessed the accounts using compromised PATs (Personal Access Token) — most likely exfiltrated silently from the victim’s development environment,” the company said. Most compromised users are located in Indonesia.
However, the exact method by which this theft may have taken place is currently unclear, although it’s suspected that it may have involved a rogue package inadvertently installed by the developers.
The development highlights the continued attempts on part of threat actors to poison open-source ecosystems and facilitate supply chain compromises.
This is evidenced by a new data exfiltration campaign targeting both npm and PyPI that uses as many as 39 counterfeit packages to gather sensitive machine information and transmit the details to a remote server.
Fight AI with AI — Battling Cyber Threats with Next-Gen AI Tools
Ready to tackle new AI-driven cybersecurity challenges? Join our insightful webinar with Zscaler to address the growing threat of generative AI in cybersecurity.
The modules, published over several days between September 12 and 24, 2023, demonstrate a progressive increase in complexity, scope, and obfuscation techniques, Phylum said.
The Israeli company is also tracking what it characterized as a large typosquat campaign aimed at npm, in which 125 packages masquerading as angular and react are being used to send machine information to a remote Discord channel.
However, the activity appears to be part of a “research project,” with the author claiming that it’s done to “find out if any of the bug bounty programs I’m participating in gets affected by one of the packages so that I could be the first one to notify them and protect their infrastructure.”
“This is in violation of the npm Acceptable Use Policy, and these sorts of campaigns put a strain on individuals tasked with keeping these ecosystems clean,” Phylum cautioned.
[ad_2]
Source link