[ad_1]
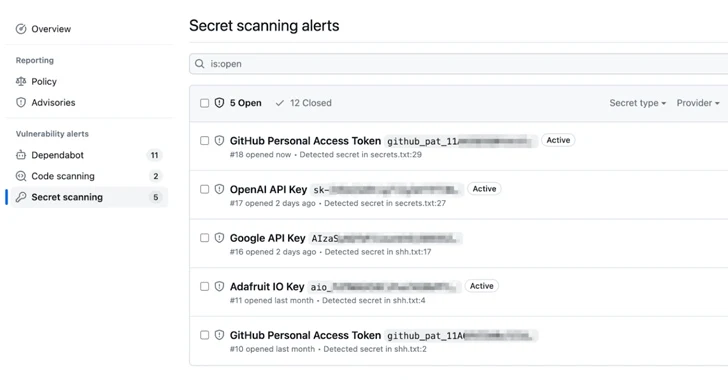
GitHub has announced an improvement to its secret scanning feature that extends validity checks to popular services such as Amazon Web Services (AWS), Microsoft, Google, and Slack.
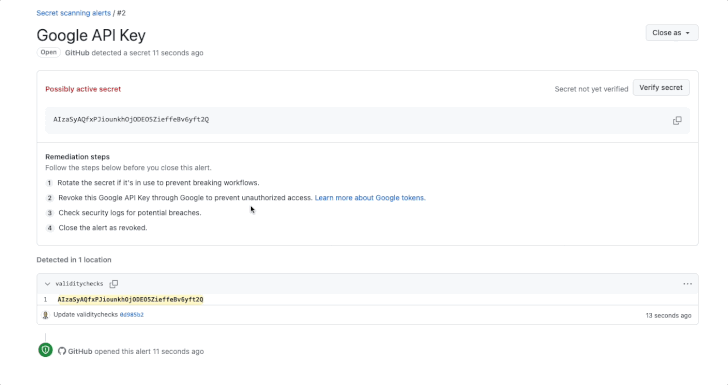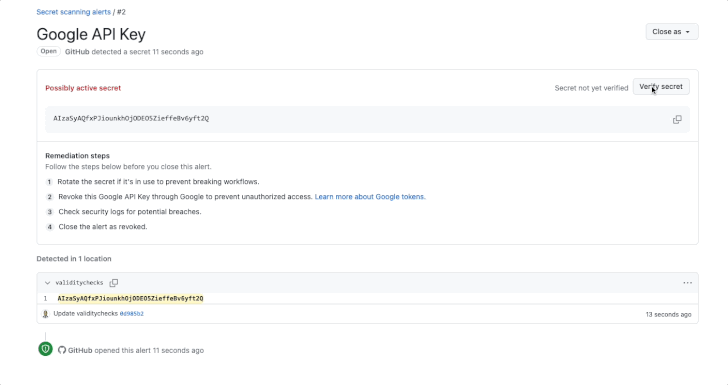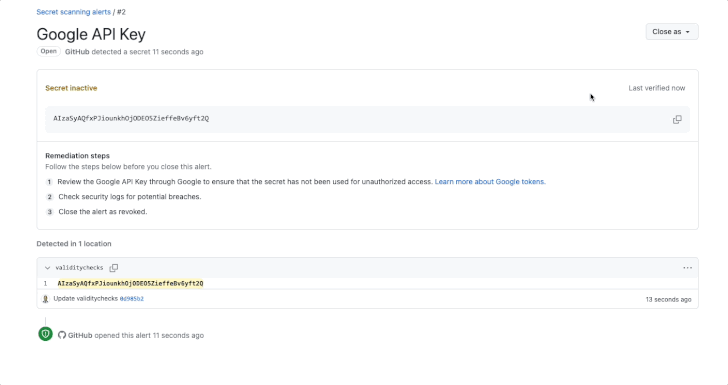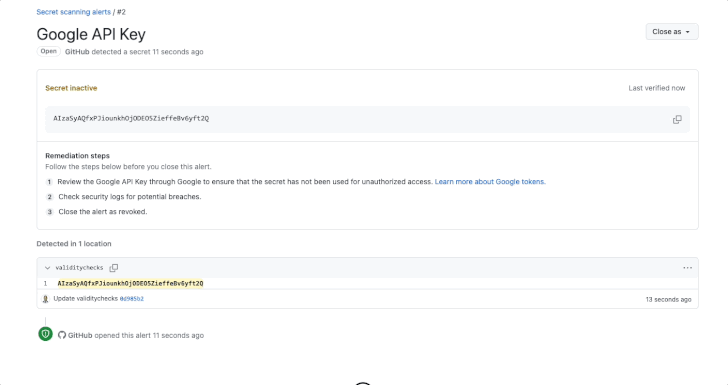
Validity checks, introduced by the Microsoft subsidiary earlier this year, alert users whether exposed tokens found by secret scanning are active, thereby allowing for effective remediation measures. It was first enabled for GitHub tokens.
The cloud-based code hosting and version control service said it intends to support more tokens in the future.
To toggle the setting, enterprise or organization owners and repository administrators can head to Settings > Code security and analysis > Secret scanning and check the option “Automatically verify if a secret is valid by sending it to the relevant partner.”
Earlier this year, GitHub also expanded secret scanning alerts for all public repositories and announced the availability of push protection to help developers and maintainers proactively secure their code by scanning for highly identifiable secrets before they are pushed.
The development comes as Amazon previewed enhanced account protection requirements that will enforce privileged users (aka root users) of an AWS Organization account to switch on multi-factor authentication (MFA) starting in mid-2024.
“MFA is one of the simplest and most effective ways to enhance account security, offering an additional layer of protection to help prevent unauthorized individuals from gaining access to systems or data,” Steve Schmidt, chief security officer at Amazon, said.
Weak or misconfigured MFA methods also found a place among the top 10 most common network misconfigurations, according to a new joint advisory issued by the U.S. National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA).
“Some forms of MFA are vulnerable to phishing, ‘push bombing,’ exploitation of Signaling System 7 (SS7) protocol vulnerabilities, and/or ‘SIM swap’ techniques,” the agencies said.
“These attempts, if successful, may allow a threat actor to gain access to MFA authentication credentials or bypass MFA and access the MFA-protected systems.”
The other prevalent cybersecurity misconfigurations are as follows –
- Default configurations of software and applications
- Improper separation of user/administrator privilege
- Insufficient internal network monitoring
- Lack of network segmentation
- Poor patch management
- Bypass of system access controls
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Unrestricted code execution
As mitigations, it’s recommended that organizations eliminate default credentials and harden configurations; disable unused services and implement access controls; prioritize patching; audit and monitor administrative accounts and privileges.
Software vendors have also been urged to implement secure by design principles, use memory-safe programming languages where possible, avoid embedding default passwords, provide high-quality audit logs to customers at no extra charge, and mandate phishing-resistant MFA methods.
“These misconfigurations illustrate (1) a trend of systemic weaknesses in many large organizations, including those with mature cyber postures, and (2) the importance of software manufacturers embracing secure-by-design principles to reduce the burden on network defenders,” the agencies noted.
[ad_2]
Source link