[ad_1]
Cybersecurity researchers have detailed an updated version of the malware HeadCrab that’s known to target Redis database servers across the world since early September 2021.
The development, which comes exactly a year after the malware was first publicly disclosed by Aqua, is a sign that the financially-motivated threat actor behind the campaign is actively adapting and refining their tactics and techniques to stay ahead of the detection curve.
The cloud security firm said that “the campaign has almost doubled the number of infected Redis servers,” with an additional 1,100 compromised servers, up from 1,200 reported at the start of 2023.
HeadCrab is designed to infiltrate internet-exposed Redis servers and wrangle them into a botnet for illicitly mining cryptocurrency, while also leveraging the access in a manner that allows the threat actor to execute shell commands, load fileless kernel modules, and exfiltrate data to a remote server.
While the origins of the threat actor are presently not known, they make it a point to note in a “mini blog” embedded into the malware that the mining activity is “legal in my country” and that they do it because “it almost doesn’t harm human life and feelings (if done right).”
The operator, however, acknowledges that it’s a “parasitic and inefficient way” of making money, adding their aim is to make $15,000 per year.
“An integral aspect of the sophistication of HeadCrab 2.0 lies in its advanced evasion techniques,” Aqua researchers Asaf Eitani and Nitzan Yaakov said. “In contrast to its predecessor (named HeadCrab 1.0), this new version employs a fileless loader mechanism, demonstrating the attacker’s commitment to stealth and persistence.”
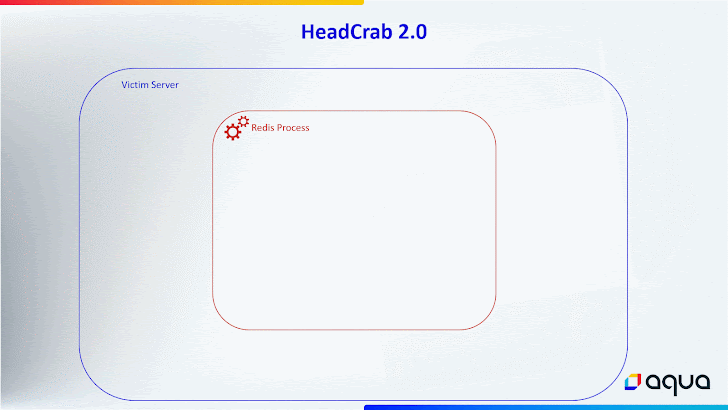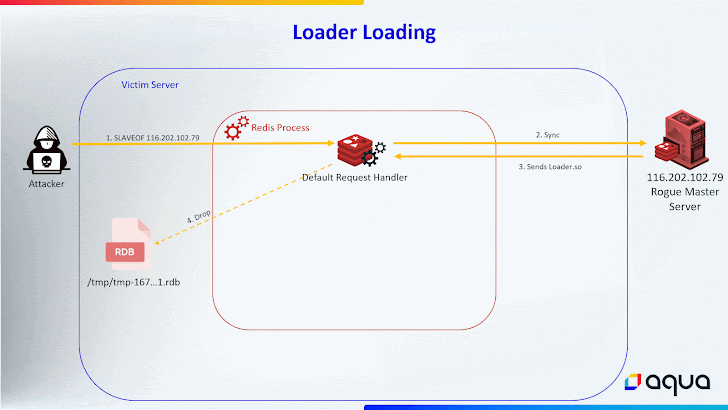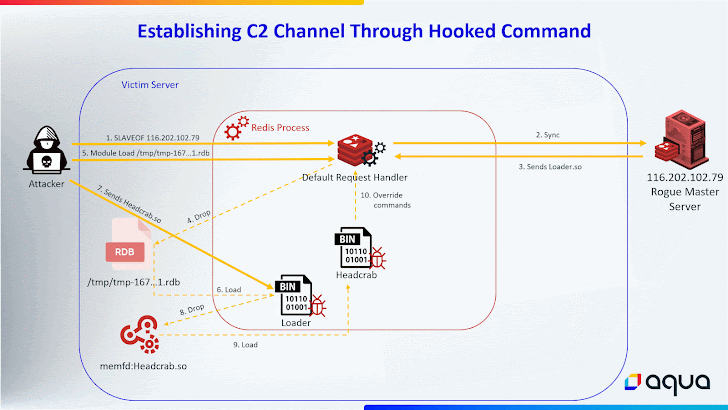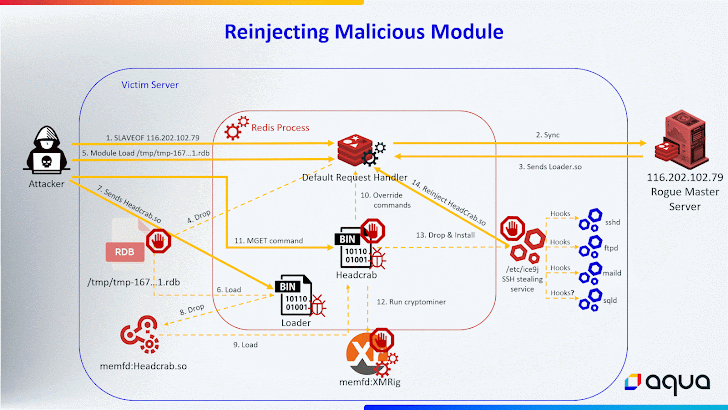
It’s worth noting that the previous iteration utilized the SLAVEOF command to download and save the HeadCrab malware file to disk, thereby leaving artifact traces on the file system.
HeadCrab 2.0, on the other hand, receives the malware’s content over the Redis communication channel and stores it in a fileless location in a bid to minimize the forensic trail and make it much more challenging to detect.
Also changed in the new variant is the use of the Redis MGET command for command-and-control (C2) communications for added covertness.
“By hooking into this standard command, the malware gains the ability to control it during specific attacker-initiated requests,” the researchers said.
“Those requests are achieved by sending a special string as an argument to the MGET command. When this specific string is detected, the malware recognizes the command as originating from the attacker, triggering the malicious C2 communication.”
Describing HeadCrab 2.0 as an escalation in the sophistication of Redis malware, Aqua said its ability to masquerade its malicious activities under the guise of legitimate commands poses new problems for detection.
“This evolution underscores the necessity for continuous research and development in security tools and practices,” the researchers concluded. “The engagement by the attacker and the subsequent evolution of the malware highlights the critical need for vigilant monitoring and intelligence gathering.”
[ad_2]
Source link