[ad_1]
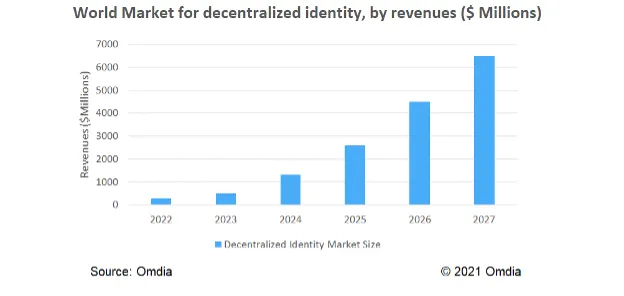
Although the decentralized identity market is still in its infancy, it has been gaining traction in recent years and has the potential to change existing identity, authentication, and access for the better. In 2022, the decentralized identity market was projected to reach $270 million.
Through decentralization and blockchain technology, there are an increasing number of people taking back control of their data. Although the digital identity space is still in its initial stages, it is possible that decentralized identity with blockchain could make identity management decentralized, simplified, and seamless, completely transforming the market landscape. Startups and DID initiatives continue to develop proofs of concept (PoC) for decentralized identity in government, finance, healthcare, and other fields, and the opportunities for decentralized identity continue to grow and evolve.
eIDAS 2.0 Driving Growth
Omdia believes that the eIDAS 2.0 regulation will be a significant driver for growth in decentralized identity during the forecast period. The updated eIDAS 2.0 initiative is built on the existing, cross-border, legal framework for trusted digital identities, the European electronic identification, and trust services initiative (eIDAS Regulation), which was adopted in 2014. By September 2023, all EU member states must ensure that a digital identity wallet is available to all EU citizens, residents, and businesses in the EU and usable not only for identity documents but for all attestations, including those with sensitive personal data such as health-related data and documents.
Advantages of Decentralized Identity
The advantages that decentralized identity gives users over traditional identity and access management solutions include control, security, privacy, and ease of use:
- Control – Control gives identity owners and digital devices power over their digital identifiers. Because users have complete control and ownership of their identities and credentials, they can decide which information they want to reveal and can prove their claims without depending on any other party.
- Security – Security reduces attack surfaces by storing personal identifiable information (PII). Blockchain is an encrypted decentralized storage system that is safe, flexible, and reduces the risk of an attacker gaining unauthorized access to steal or monetize user data.
- Privacy – Privacy enables entities to use the principle of least privilege (PoLP) to designate minimal or selective access for identity credentials. PoLP is a term correlated with information security. It states that any person, gadget, or process should only have the minimal rights necessary to execute the considered task.
- Ease of use – Decentralized identity technology gives users the advantage of easily creating and managing their identities with user-friendly neoteric decentralized identity apps and platforms.
Disadvantages of Decentralized Identity
In contrast, the disadvantages of decentralized identity include no large-scale adoption, legacy systems, and regulation and identity data fragility:
- No large-scale adoption – Governments and organizations are still attempting to figure out how to deploy decentralized identity technology at scale while most non-tech users have not even heard of this phenomenon.
- Legacy systems and regulation – Replacing existing legacy systems and creating interoperable global standards and governance are also important issues.
- Identity data fragility – While a secondary issue, identity data fragility, which refers to duplication, confusion, and inaccuracy in identity management, remains.
More Decentralized Identity Products Coming
The popularity of decentralized identity is gathering pace with vendors such as IBM, Microsoft, and Ping Identity entering the fray. Even governments are looking at the technology. Omdia believes that over the next couple of years, more decentralized identity products will be launched onto the market, and this will help the technology become more mainstream. The decentralized identity market is expected to have significant growth during the forecast period, increasing to $6.5 billion in 2027.
[ad_2]
Source link
