[ad_1]
Cyberattackers are doubling down on their attacks against law firms and corporate legal departments, moving beyond their historical activity of hacking and leaking secrets to targeting the sector with financial attacks, such as ransomware and business email compromise (BEC).
On Nov. 24, managed service provider CTS, which provides IT services to law firms, acknowledged that the firm had suffered a breach, but did not give details about the source of the attack. The incident has reportedly affected services to dozens of law firms, particularly in the real estate sector. The attack follows claims by the LockBit group that it compromised London-based law firm Allen & Overy, listing the firm among the victims on its data-leak site and demanding a ransom. The firm confirmed a breach, but did not acknowledge the ransomware attack.
The attacks are only the latest to target law firms and legal departments. At least one attack group has targeted law firms specifically, seeding compromised sites with legal jargon to make the sites rise in search rankings and then deliver a ransomware attack chain to visitors, says Keegan Keplinger, a senior security researcher with managed detection and response firm eSentire.
“When [the targeting] hasn’t been a legal organization, it’s often been the legal department or a legal user — a paralegal or the legal consultant — in an organization,” he says. “We saw a hospital get hit once, but it was the legal user in that hospital that downloaded [the malware].”
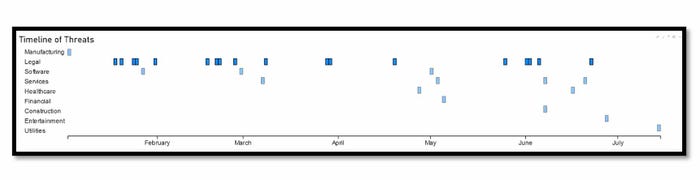
GootLoader, which leads to Blackcat ransomware, has focused heavily on law firms. Source: eSentire
Hackers have long favored law firms as a way to steal secrets, absconding with Uber drivers’ personal information from law firm Genova Burns LLC in January; hijacking data on the contracts and personal emails from 200 high-profile celebrities — including Lady Gaga, Madonna, and Rod Stewart — from New York law firm Grubman Shire Meiselas & Sacks in 2020; and allegedly leaking the “Panama Papers” — 11.5 million documents on wealthy tax evaders — from Panama-based law firm Mossack Fonseca.
Traditionally, the attraction for online attackers has not been money, says Ilia Kolochenko, chief architect at application security firm ImmuniWeb.
“Law firms are pretty far from being attractive victims for cybercriminals,” he says. “However, their clients — namely, secrets of their clients — make law firms a magnet for all kind of cybercriminals.”
Clickbait Turns to SEO Poisoning
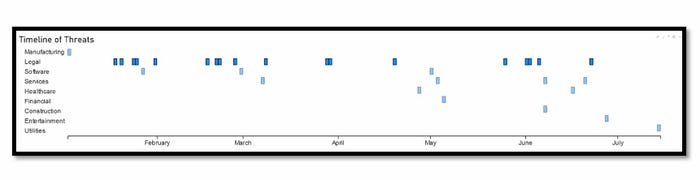
That has changed, as cybercriminals increasingly focus on law firms as a way to cash in with ransomware and BEC attacks. More than a quarter of law firms (27%) suffered a security breach in 2022, up from 25% in 2021, according to the American Bar Association’s annual cybersecurity report, which stresses that a security breach is not as severe a classification as a data breach. The legal sector is the fourth most targeted sector by cybercriminals — behind services, manufacturing, and financial firms, according to eSentire’s data.
The most significant threat to law firms may be GootLoader, a browser-based threat that is delivered through search engine optimization (SEO) poisoning. The group behind GootLoader has seeded malicious content and malvertising linked to 3.5 million search terms, a high percentage of which are legal terms. As a result, a lawyer or paralegal who searches for specific content may find the top search result leading to a GootLoader-infected file. Downloading and opening the file will execute the program, which almost always leads to BlackCat ransomware, says Joe Stewart, a principal security researcher at eSentire.
“This [is] what I call a landmine approach,” he says. “They’re just mining the entire Web with these search keywords and just waiting for somebody in the legal profession, or somebody who needs this legal document, to just stumble on it and open it up, say, ‘What’s this? Oh, I will click on this JavaScript. No problem.'”
Ransomware is not the only worry for law firms. A number of threat groups are also targeting law firms with BEC scams. Law firms are the perfect victims for such schemes, says Dan Caplin, director of cybersecurity and incident response at S-RM, a cybersecurity consultancy.
“Firstly, they do a lot of business over and in emails, and secondly, law firms often occupy a privileged position in situations where payment instructions and details are exchanged — this, again, is mostly done over email,” he says. “This makes email account takeover, intercepting a thread about a legitimate payment, and diverting funds to a fraudulent bank account a really effective approach.”
Will Get Worse Before It Gets Better
Because law firms tend to be smaller, often just one or two people, cybersecurity knowledge is often lacking, says ImmuniWeb’s Kolochenko.
“Solo practitioners and small law firms are usually poorly protected, having very modest budgets for cybersecurity,” he says. “Large law firms, however, increasingly spend more on cybersecurity and cyber defense, [but most firms] have similar problems as all other industries including shadow IT, working from home, [and] underprotected third parties.”
Unfortunately, law firms are often tasked as the custodian of extremely sensitive information, making any breach a problem and making the firm more likely to pay a ransom. It’s little wonder that GootLoader has targeted the industry, says eSentire’s Keplinger.
“For a variety of reasons, law firms are behind the curve a little bit on security,” he says. “With ransomware — especially the double whammy (both stealing and encrypting the data) — legal firms are an obvious organization that would be vulnerable to that — especially, that would care about publishing their data.”
[ad_2]
Source link