[ad_1]
The notorious North Korean state-backed hacking group Lazarus uploaded four packages to the Python Package Index (PyPI) repository with the goal of infecting developer systems with malware.
The packages, now taken down, are pycryptoenv, pycryptoconf, quasarlib, and swapmempool. They have been collectively downloaded 3,269 times, with pycryptoconf accounting for the most downloads at 1,351.
“The package names pycryptoenv and pycryptoconf are similar to pycrypto, which is a Python package used for encryption algorithms in Python,” JPCERT/CC researcher Shusei Tomonaga said. “Therefore, the attacker probably prepared the malware-containing malicious packages to target users’ typos in installing Python packages.”
The disclosure comes days after Phylum uncovered several rogue packages on the npm registry that have been used to single out software developers as part of a campaign codenamed Contagious Interview.
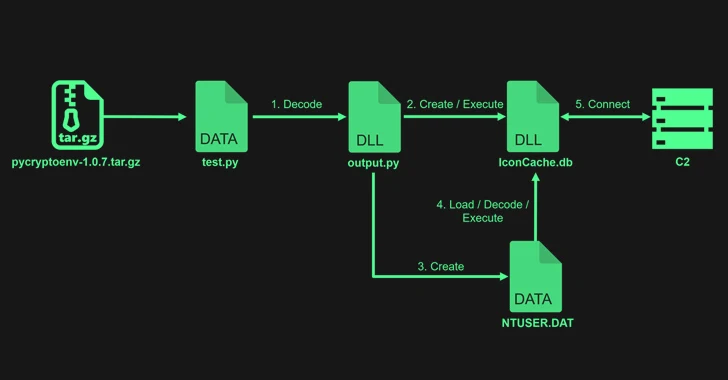
An interesting commonality between the two sets of attacks is that the malicious code is concealed within a test script (“test.py”). In this case, however, the test file is merely a smokescreen for what’s an XOR-encoded DLL file, which, in turn, creates two DLL files named IconCache.db and NTUSER.DAT.
The attack sequence then uses NTUSER.DAT to load and execute IconCache.db, a malware called Comebacker that’s responsible for establishing connections with a command-and-control (C2) server to fetch and run a Windows executable file.
JPCERT/CC said the packages are a continuation of a campaign that Phylum first detailed in November 2023 as leveraging crypto-themed npm modules to deliver Comebacker.
“Attackers may be targeting users’ typos to have the malware downloaded,” Tomonaga said. “When you install modules and other kinds of software in your development environment, please do so carefully to avoid installing unwanted packages.”
[ad_2]
Source link