[ad_1]
The North Korea-linked Lazarus Group (aka Hidden Cobra or TEMP.Hermit) has been observed using trojanized versions of Virtual Network Computing (VNC) apps as lures to target the defense industry and nuclear engineers as part of a long-running campaign known as Operation Dream Job.
“The threat actor tricks job seekers on social media into opening malicious apps for fake job interviews,” Kaspersky said in its APT trends report for Q3 2023.
“To avoid detection by behavior-based security solutions, this backdoored application operates discreetly, only activating when the user selects a server from the drop-down menu of the Trojanized VNC client.”
Once launched by the victim, the counterfeit app is designed to retrieve additional payloads, including a known Lazarus Group malware dubbed LPEClient, which comes fitted with capabilities to profile compromised hosts.
Also deployed by the adversary is an updated version of COPPERHEDGE, a backdoor known for running arbitrary commands, performing system reconnaissance, and exfiltrating data, as well as a bespoke malware specifically meant for transmitting files of interest to a remote server.
Targets of the latest campaign comprise businesses that are directly involved in defense manufacturing, including radar systems, unmanned aerial vehicles (UAVs), military vehicles, ships, weaponry, and maritime companies.
Operation Dream Job refers to a series of attacks orchestrated by the North Korean hacking outfit in which potential targets are contacted via suspicious accounts via various platforms such as LinkedIn, Telegram, and WhatsApp under the pretext of offering lucrative job opportunities to trick them into installing malware.
Late last month, ESET revealed details of a Lazarus Group attack aimed at an unnamed aerospace company in Spain in which employees of the firm were approached by the threat actor posing as a recruiter for Meta on LinkedIn to deliver an implant named LightlessCan.
Lazarus Group is just one of the many offensive programs originating from North Korea that have been linked to cyber espionage and financially motivated thefts.
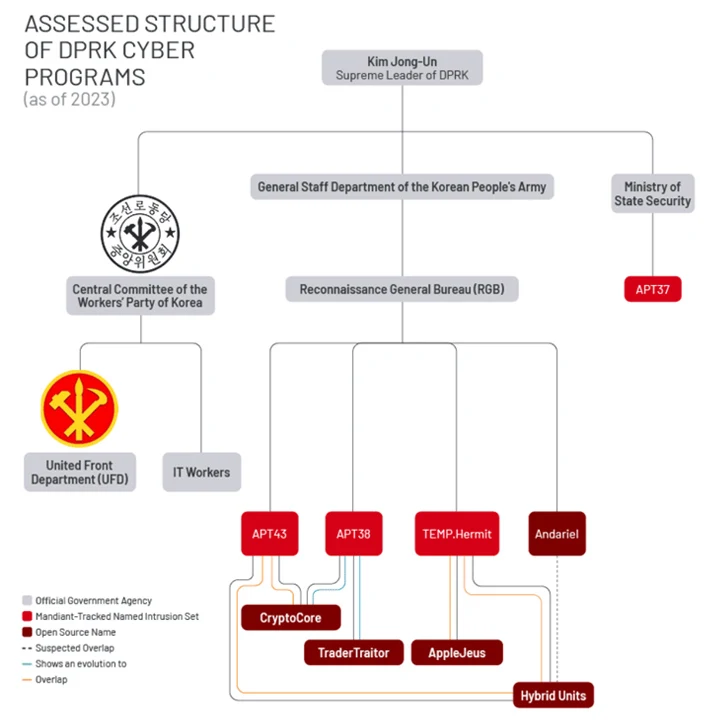
Another prominent hacking crew is APT37 (aka ScarCruft), which is part of the Ministry of State Security, unlike other threat activity clusters – i.e., APT43, Kimsuky, and Lazarus Group (and its sub-groups Andariel and BlueNoroff) – that are affiliated with the Reconnaissance General Bureau (RGB).
“While different threat groups share tooling and code, North Korean threat activity continues to adapt and change to build tailored malware for different platforms, including Linux and macOS,” Google-owned Mandiant disclosed earlier this month, highlighting their evolution in terms of adaptability and complexity.
ScarCruft, per Kaspersky, targeted a trading company linked to Russia and North Korea using a novel phishing attack chain that culminated in the delivery of RokRAT (aka BlueLight) malware, underscoring ongoing attempts by the hermit kingdom to target Russia.
What’s more, another noticeable shift is the infrastructure, tooling, and targeting overlaps between various North Korean hacking outfits like Andariel, APT38, Lazarus Group, and APT43, muddying attribution efforts and pointing to a streamlining of adversarial activities.
This has also been accompanied by an “increased interest in the development of macOS malware to backdoor platforms of high value targets within the cryptocurrency and the blockchain industries,” Mandiant said.
[ad_2]
Source link