[ad_1]
The threat actors behind the Monti ransomware have resurfaced after a two-month break with a new Linux version of the encryptor in its attacks targeting government and legal sectors.
Monti emerged in June 2022, weeks after the Conti ransomware group shut down its operations, deliberately imitating the tactics and tools associated with the latter, including its leaked source code. Not anymore.
The new version, per Trend Micro, is a departure of sorts, exhibiting significant changes from its other Linux-based predecessors.
“Unlike the earlier variant, which is primarily based on the leaked Conti source code, this new version employs a different encryptor with additional distinct behaviors,” Trend Micro researchers Nathaniel Morales and Joshua Paul Ignacio said.
A BinDiff analysis has revealed that while the older iterations had a 99% similarity rate with Conti, the latest version has only a 29% similarity rate, suggesting an overhaul.

Some of the crucial changes include the addition of a ‘–whitelist’ parameter to instruct the locker to skip a list of virtual machines as well as the removal of command-line arguments –size, –log, and –vmlist.
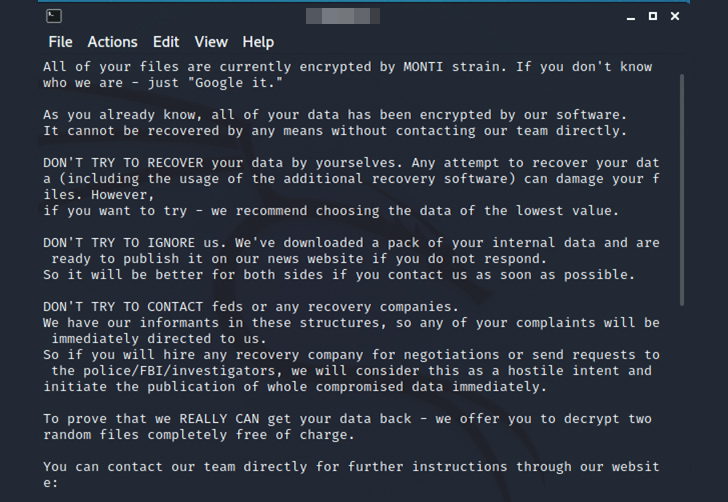
The Linux variant is also designed to tamper with the motd (aka message of the day) file to display the ransom note, employ AES-256-CTR encryption instead of Salsa20, and solely rely on the file size for its encryption process.
In other words, files larger than 1.048 MB but smaller than 4.19 MB will only have the first 100,000 (0xFFFFF) bytes of the file encrypted, while those exceeding 4.19 MB have a chunk of their content locked depending on the outcoming of a Shift Right operation.
Files that have a size smaller than 1.048 MB will have all their contents encrypted.
“It’s likely that the threat actors behind Monti still employed parts of the Conti source code as the base for the new variant, as evidenced by some similar functions, but implemented significant changes to the code — especially to the encryption algorithm,” the researchers said.
“Furthermore, by altering the code, Monti’s operators are enhancing its ability to evade detection, making their malicious activities even more challenging to identify and mitigate.”
[ad_2]
Source link