[ad_1]
The North Korea-aligned Lazarus Group has been attributed as behind a new campaign in which an unnamed software vendor was compromised through the exploitation of known security flaws in another high-profile software.
The attack sequences, according to Kaspersky, culminated in the deployment of malware families such as SIGNBT and LPEClient, a known hacking tool used by the threat actor for victim profiling and payload delivery.
“The adversary demonstrated a high level of sophistication, employing advanced evasion techniques and introducing SIGNBT malware for victim control,” security researcher Seongsu Park said. “The SIGNBT malware used in this attack employed a diverse infection chain and sophisticated techniques.”
The Russian cybersecurity vendor said the company that developed the exploited software had been a victim of a Lazarus attack several times, indicating an attempt to steal source code or poison the software supply chain, as in the case of the 3CX supply chain attack.
The Lazarus Group “continued to exploit vulnerabilities in the company’s software while targeting other software makers,” Park added. As part of the latest activity, a number of victims are said to have been singled out as of mid-July 2023.
The victims, per the company, were targeted through a legitimate security software designed to encrypt web communications using digital certificates. The name of the software was not disclosed and the exact mechanism by which the software was weaponized to distribute SIGNBT remains unknown.
Besides relying on various tactics to establish and maintain persistence on compromised systems, the attack chains employ an in-memory loader that acts as a conduit to launch the SIGNBT malware.
The main function of SIGNBT is to establish contact with a remote server and retrieve further commands for execution on the infected host. The malware is so named for its use of distinctive strings that are prefixed with “SIGNBT” in its HTTP-based command-and-control (C2) communications –
- SIGNBTLG, for initial connection
- SIGNBTKE, for gathering system metadata upon receiving a SUCCESS message from the C2 server
- SIGNBTGC, for fetching commands
- SIGNBTFI, for communication failure
- SIGNBTSR, for a successful communication
The Windows backdoor, for its part, is armed with a wide range of capabilities to exert control over the victim’s system. This includes process enumeration, file and directory operations, and the deployment of payloads such as LPEClient and other credential-dumping utilities.
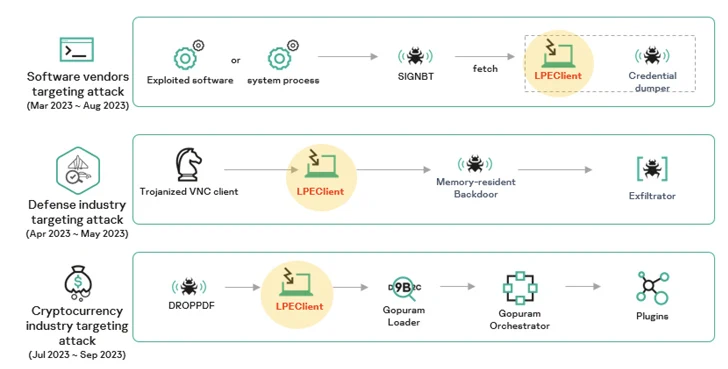
Kaspersky said it identified at least three disparate Lazarus campaigns in 2023 using varied intrusion vectors and infection procedures, but consistently relied on LPEClient malware to deliver the final-stage malware.
One such campaign paved the way for an implant codenamed Gopuram, which was used in cyber assaults targeting cryptocurrency companies by leveraging a trojanized version of the 3CX voice and video conferencing software.
The latest findings are just the latest example of North Korean-linked cyber operations, in addition to being a testament to the Lazarus Group’s ever-evolving and ever-expanding arsenal of tools, tactics, and techniques.
“The Lazarus Group remains a highly active and versatile threat actor in today’s cybersecurity landscape,” Park said.
“The threat actor has demonstrated a profound understanding of IT environments, refining their tactics to include exploiting vulnerabilities in high-profile software. This approach allows them to efficiently spread their malware once initial infections are achieved.”
[ad_2]
Source link