[ad_1]
Spanish-speaking users in Latin America have been at the receiving end of a new botnet malware dubbed Horabot since at least November 2020.
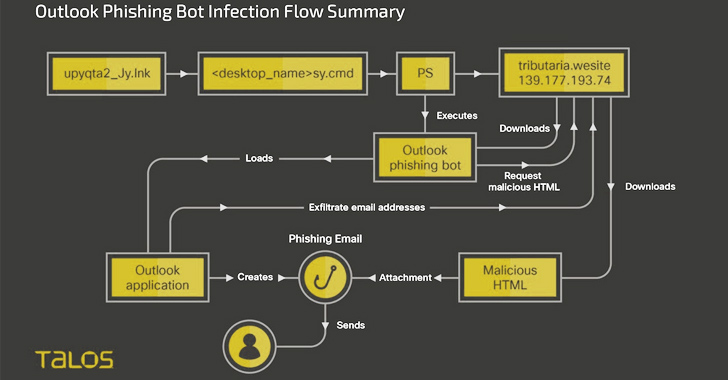
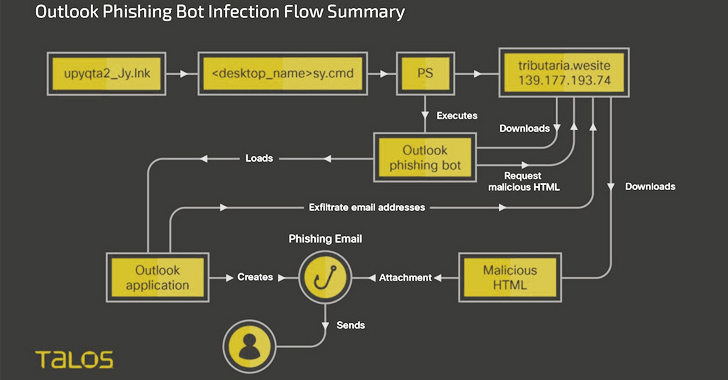
“Horabot enables the threat actor to control the victim’s Outlook mailbox, exfiltrate contacts’ email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim’s mailbox,” Cisco Talos researcher Chetan Raghuprasad said.
The botnet program also delivers a Windows-based financial trojan and a spam tool to harvest online banking credentials as well as compromise Gmail, Outlook, and Yahoo! webmail accounts to blast spam emails.
The cybersecurity firm said a majority of the infections are located in Mexico, with limited victims identified in Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama. The threat actor behind the campaign is believed to be in Brazil.
Targeted users of the ongoing campaign primarily span accounting, construction and engineering, wholesale distribution, and investment verticals, although it’s suspected that other sectors in the region may also be affected.
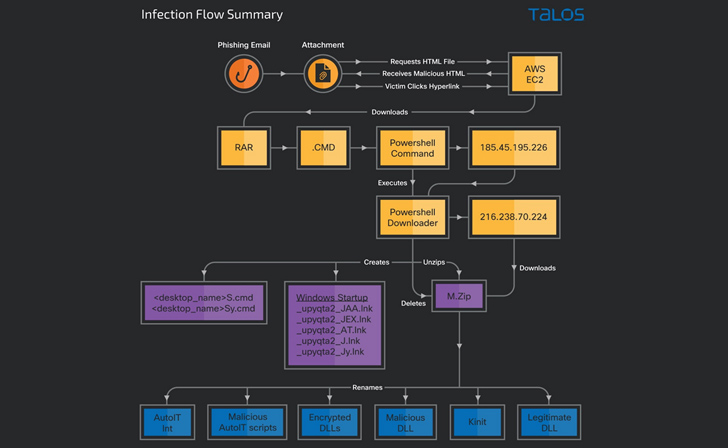
The attacks start with phishing emails bearing tax-themed lures that entice the recipients into opening an HTML attachment, which, in turn, embeds a link containing a RAR archive.
Opening the contents of the file results in the execution of a PowerShell downloader script that’s responsible for retrieving a ZIP file containing the main payloads from a remote server and rebooting the machine.
The system restart also serves as a launchpad for the banking trojan and the spam tool, allowing the threat actor to steal data, log keystrokes, capture screenshots, and disseminate additional phishing emails to the victim’s contacts.
“This campaign involves a multi-stage attack chain that begins with a phishing email and leads to payload delivery through the execution of a PowerShell downloader script and sideloading to legitimate executables,” Raghuprasad said.
The banking trojan is a 32-bit Windows DLL written in the Delphi programming language, and shares overlaps with other Brazilian malware families like Mekotio and Casbaneiro.
Horabot, for its part, is an Outlook phishing botnet program written in PowerShell that’s capable of sending phishing emails to all email addresses in the victim’s mailbox to propagate the infection. It’s also a deliberate attempt to minimize the threat actor’s phishing infrastructure from being exposed.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
The disclosure arrives a week after SentinelOne attributed an unknown Brazilian threat actor to a long-running campaign targeting more than 30 Portuguese financial institutions with information-stealing malware since 2021.
It also follows the discovery of a new Android banking trojan dubbed PixBankBot that abuses the operating system’s accessibility services to conduct fraudulent money transfers over the Brazilian PIX payments platform.
PixBankBot is also the latest example of malware that specifically focuses on Brazilian banks, featuring capabilities similar to BrasDex, PixPirate, and GoatRAT that have been spotted in recent months.
If anything, the developments represent yet another iteration of a broader group of financially motivated hacking efforts emanating from Brazil, making it crucial that users remain vigilant to avoid falling prey to such threats.
[ad_2]
Source link