[ad_1]
The threat actor known as ChamelGang has been observed using a previously undocumented implant to backdoor Linux systems, marking a new expansion of the threat actor’s capabilities.
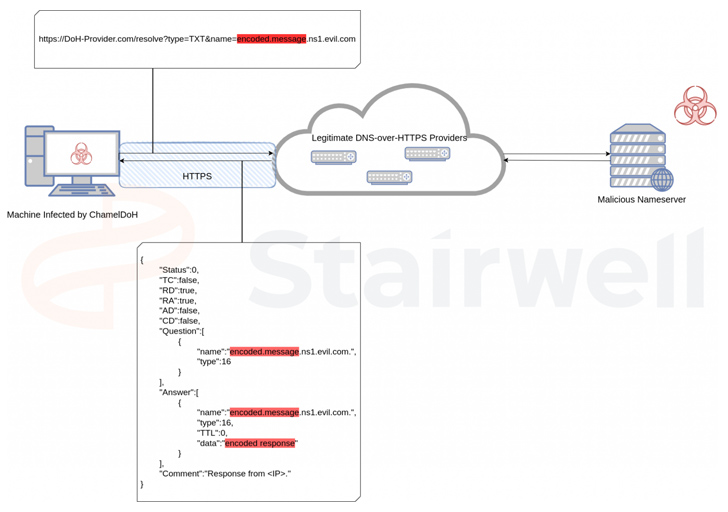
The malware, dubbed ChamelDoH by Stairwell, is a C++-based tool for communicating via DNS-over-HTTPS (DoH) tunneling.
ChamelGang was first outed by Russian cybersecurity firm Positive Technologies in September 2021, detailing its attacks on fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan.
Attack chains mounted by the actor have leveraged vulnerabilities in Microsoft Exchange servers and Red Hat JBoss Enterprise Application to gain initial access and carry out data theft attacks using a passive backdoor called DoorMe.
“This is a native IIS module that is registered as a filter through which HTTP requests and responses are processed,” Positive Technologies said at the time. “Its principle of operation is unusual: the backdoor processes only those requests in which the correct cookie parameter is set.”
The Linux backdoor discovered by Stairwell, for its part, is designed to capture system information and is capable of remote access operations such as file upload, download, deletion, and shell command execution.
What makes ChamelDoH unique is its novel communication method of using DoH, which is used to perform Domain Name System (DNS) resolution via the HTTPS protocol, to send DNS TXT requests to a rogue nameserver.
“Due to these DoH providers being commonly utilized DNS servers [i.e., Cloudflare and Google] for legitimate traffic, they cannot easily be blocked enterprise-wide,” Stairwell researcher Daniel Mayer said.
The use of DoH for command-and-control (C2) also offers additional benefits for the threat actor in that the requests cannot be intercepted by means of an adversary-in-the-middle (AitM) attack owing to the use of the HTTPS protocol.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
This also means that security solutions cannot identify and prohibit malicious DoH requests and sever the communications, thereby turning it to an encrypted channel between a compromised host and the C2 server.
“The result of this tactic is akin to C2 via domain fronting, where traffic is sent to a legitimate service hosted on a CDN, but redirected to a C2 server via the request’s Host header – both detection and prevention are difficult,” Mayer explained.
The California-based cybersecurity firm said it detected a total of 10 ChamelDoH samples on VirusTotal, one of which was uploaded back on December 14, 2022.
The latest findings show that the “group has also devoted considerable time and effort to researching and developing an equally robust toolset for Linux intrusions,” Mayer said.
[ad_2]
Source link