[ad_1]
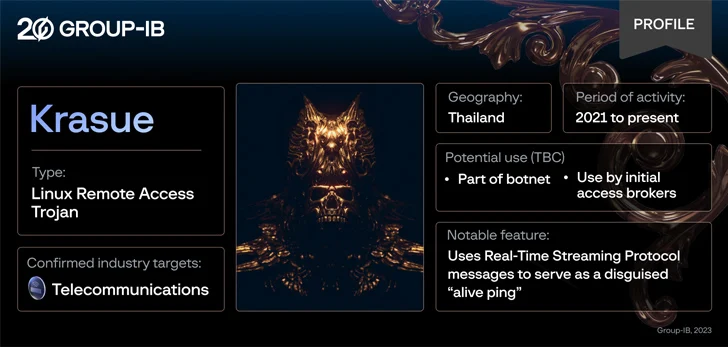
A previously unknown Linux remote access trojan called Krasue has been observed targeting telecom companies in Thailand by threat actors to main covert access to victim networks at lease since 2021.
Named after a nocturnal female spirit of Southeast Asian folklore, the malware is “able to conceal its own presence during the initialization phase,” Group-IB said in a report shared with The Hacker News.
The exact initial access vector used to deploy Krasue is currently not known, although it’s suspected that it could be via vulnerability exploitation, credential brute-force attacks, or downloaded as part of a bogus software package or binary. The scale of the campaign is
Cracking the Code: Learn How Cyber Attackers Exploit Human Psychology
Ever wondered why social engineering is so effective? Dive deep into the psychology of cyber attackers in our upcoming webinar.
The malware’s core functionalities are realized through a rootkit that allows it to maintain persistence on the host without attracting any attention. The rootkit is derived from open-source projects such as Diamorphine, Suterusu, and Rooty.
This has raised the possibility that Krasue is either deployed as part of a botnet or sold by initial access brokers to other cybercriminals, such as ransomware affiliates, who are looking to obtain access to a specific target.
“The rootkit can hook the `kill()` syscall, network-related functions, and file listing operations in order to hide its activities and evade detection,” Group-IB malware analyst Sharmine Low said.
“Notably, Krasue uses RTSP (Real Time Streaming Protocol) messages to serve as a disguised ‘alive ping,’ a tactic rarely seen in the wild.”
The trojan’s command-and-control (C2) communications further allow it to designate a communicating IP as its master upstream C2 server, get information about the malware, and even terminate itself.
Krasue also shares several source code similarities with another Linux malware named XorDdos, indicating that it has been developed by the same author as the latter, or by actors who had access to its source code.
“The information available is not enough to put forward a conclusive attribution as to the creator of Krasue, or the groups that are leveraging it in the wild, but the fact that these malicious programs are able to remain under the radar for extended periods makes it clear that continuous vigilance and better security measures are necessary,” Low said.
[ad_2]
Source link