[ad_1]
Poorly secured Linux SSH servers are being targeted by bad actors to install port scanners and dictionary attack tools with the goal of targeting other vulnerable servers and co-opting them into a network to carry out cryptocurrency mining and distributed denial-of-service (DDoS) attacks.
“Threat actors can also choose to install only scanners and sell the breached IP and account credentials on the dark web,” the AhnLab Security Emergency Response Center (ASEC) said in a report on Tuesday.
In these attacks, adversaries try to guess a server’s SSH credentials by running through a list of commonly used combinations of usernames and passwords, a technique called dictionary attack.
Should the brute-force attempt be successful, it’s followed by the threat actor deploying other malware, including scanners, to scan for other susceptible systems on the internet.
Specifically, the scanner is designed to look for systems where port 22 — which is associated with the SSH service — is active and then repeats the process of staging a dictionary attack in order to install malware, effectively propagating the infection.
Another notable aspect of the attack is the execution of commands such as “grep -c ^processor /proc/cpuinfo” to determine the number of CPU cores.
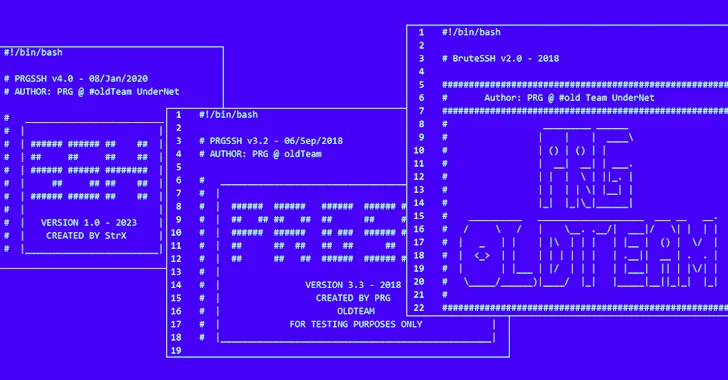
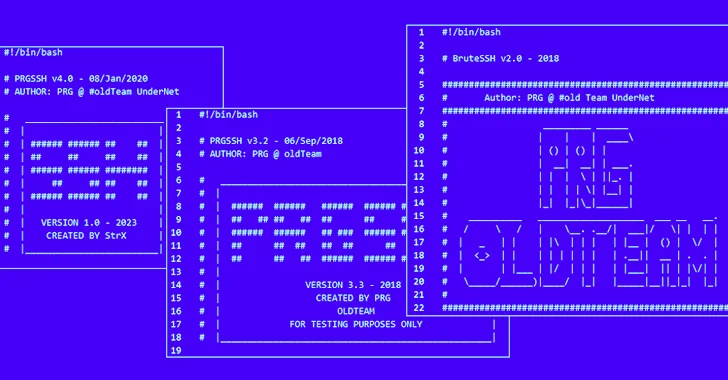
“These tools are believed to have been created by PRG old Team, and each threat actor modifies them slightly before using them in attacks,” ASEC said, adding there is evidence of such malicious software being used as early as 2021.
To mitigate the risks associated with these attacks, it’s recommended that users rely on passwords that are hard to guess, periodically rotate them, and keep their systems up-to-date.
The findings come as Kaspersky revealed that a novel multi-platform threat called NKAbuse is leveraging a decentralized, peer-to-peer network connectivity protocol known as NKN (short for New Kind of Network) as a communications channel for DDoS attacks.
[ad_2]
Source link