[ad_1]
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID.
Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its “User-Agent” string.
Both Bumblebee and IcedID serve as loaders, acting as a vector for other malware on compromised hosts, including ransomware. A recent report from Proofpoint highlighted IcedID’s abandoning of banking fraud features to solely focus on malware delivery.
Bumblebee, notably, is a replacement for another loader called BazarLoader, which has been attributed to the now-defunct TrickBot and Conti groups.
A report from Secureworks in April 2022 found evidence of collaboration between several actors in the Russian cybercrime ecosystem, including that of Conti, Emotet, and IcedID.
Deep Instinct’s source code analysis of PindOS shows that it contains comments in Russian, raising the possibility of a continued partnership between the e-crime groups.
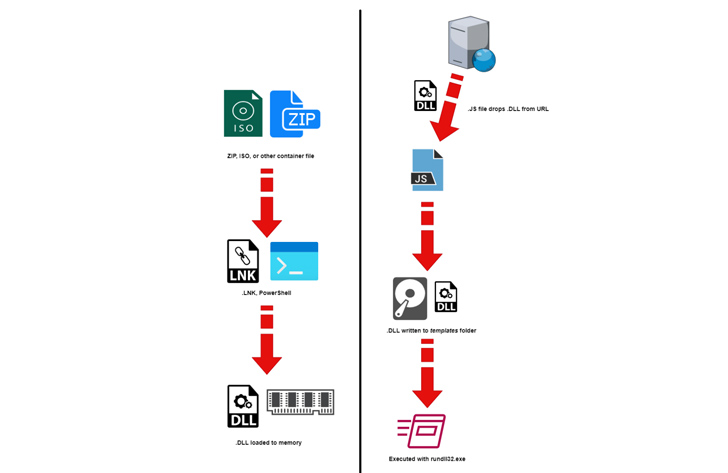
Described as a “surprisingly simple” loader, it’s designed to download malicious executables from a remote server. It makes use of two URLs, one of which functions as a fallback in the event the first URL fails to fetch the DLL payload.
“The retrieved payloads are generated pseudo-randomly ‘on-demand’ which results in a new sample hash each time a payload is fetched,” security researchers Shaul Vilkomir-Preisman and Mark Vaitzman said.
The DLL files are ultimately launched using rundll32.exe, a legitimate Windows tool to load and run DLLs.
“Whether PindOS is permanently adopted by the actors behind Bumblebee and IcedID remains to be seen,” the researchers concluded.
“If this ‘experiment’ is successful for each of these ‘companion’ malware operators it may become a permanent tool in their arsenal and gain popularity among other threat actors.”
[ad_2]
Source link