[ad_1]
Cybersecurity researchers have uncovered an “implementation vulnerability” that has made it possible to reconstruct encryption keys and decrypt data locked by Rhysida ransomware.
The findings were published last week by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA).
“Through a comprehensive analysis of Rhysida Ransomware, we identified an implementation vulnerability, enabling us to regenerate the encryption key used by the malware,” the researchers said.
The development marks the first successful decryption of the ransomware strain, which first made its appearance in May 2023. A recovery tool is being distributed through KISA.
The study is also the latest to achieve data decryption by exploiting implementation vulnerabilities in ransomware, after Magniber v2, Ragnar Locker, Avaddon, and Hive.
Rhysida, which is known to share overlaps with another ransomware crew called Vice Society, leverages a tactic known as double extortion to apply pressure on victims into paying up by threatening to release their stolen data.
An advisory published by the U.S. government in November 2023 called out the threat actors for staging opportunistic attacks targeting education, manufacturing, information technology, and government sectors.
A thorough examination of the ransomware’s inner workings has revealed its use of LibTomCrypt for encryption as well as parallel processing to speed up the process. It has also been found to implement intermittent encryption (aka partial encryption) to evade detection by security solutions.
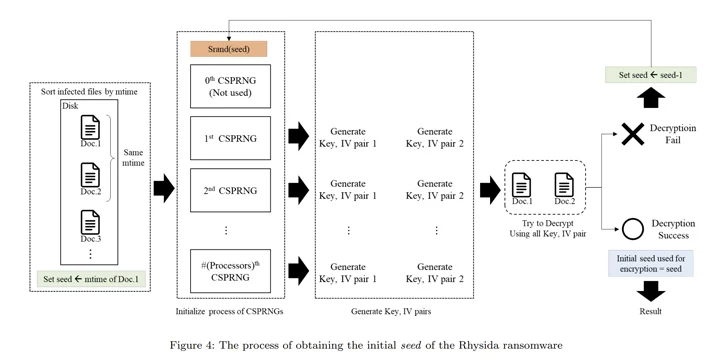
“Rhysida ransomware uses a cryptographically secure pseudo-random number generator (CSPRNG) to generate the encryption key,” the researchers said. “This generator uses a cryptographically secure algorithm to generate random numbers.”
Specifically, the CSPRNG is based on the ChaCha20 algorithm provided by the LibTomCrypt library, with the random number generated also correlated to the time at which Rhysida ransomware is running.
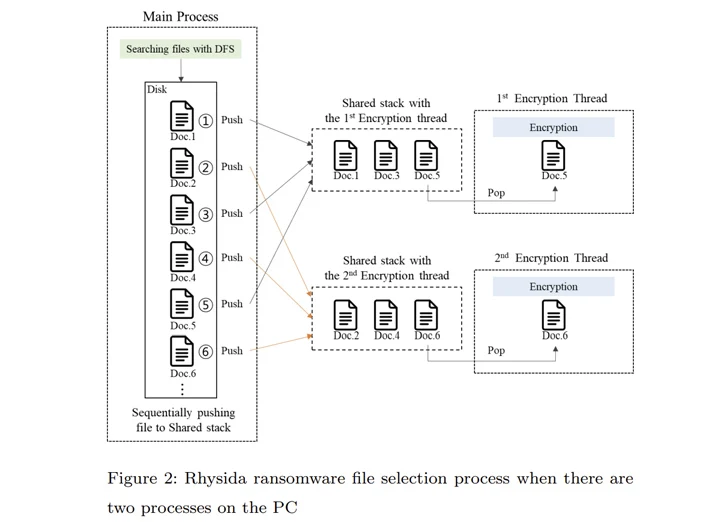
That’s not all. The main process of Rhysida ransomware compiles a list of files to be encrypted. This list is subsequently referenced by various threads created to simultaneously encrypt the files in a specific order.
“In the encryption process of the Rhysida ransomware, the encryption thread generates 80 bytes of random numbers when encrypting a single file,” the researchers noted. “Of these, the first 48 bytes are used as the encryption key and the [initialization vector].”
Using these observations as reference points, the researchers said they were able to retrieve the initial seed for decrypting the ransomware, determine the “randomized” order in which the files were encrypted, and ultimately recover the data without having to pay a ransom.
“Although these studies have a limited scope, it is important to acknowledge that certain ransomwares […] can be successfully decrypted,” the researchers concluded.
[ad_2]
Source link