[ad_1]
Governmental entities in the Middle East and Africa have been at the receiving end of sustained cyber-espionage attacks that leverage never-before-seen and rare credential theft and Exchange email exfiltration techniques.
“The main goal of the attacks was to obtain highly confidential and sensitive information, specifically related to politicians, military activities, and ministries of foreign affairs,” Lior Rochberger, senior threat researcher at Palo Alto Networks, said in a technical deep dive published last week.
The company’s Cortex Threat Research team is tracking the activity under the temporary name CL-STA-0043 (where CL stands for cluster and STA stands for state-backed motivation), describing it as a “true advanced persistent threat.”
The infection chain is triggered by the exploitation of vulnerable on-premises Internet Information Services (IIS) and Microsoft Exchange serves to infiltrate target networks.
Palo Alto Networks said it detected failed attempts to execute the China Chopper web shell in one of the attacks, prompting the adversary to shift tactics and leverage an in-memory Visual Basic Script implant from the Exchange Server.
A successful break-in is followed by reconnaissance activity to map out the network and single out critical servers that hold data of value, including domain controllers, web servers, Exchange servers, FTP servers, and SQL databases.
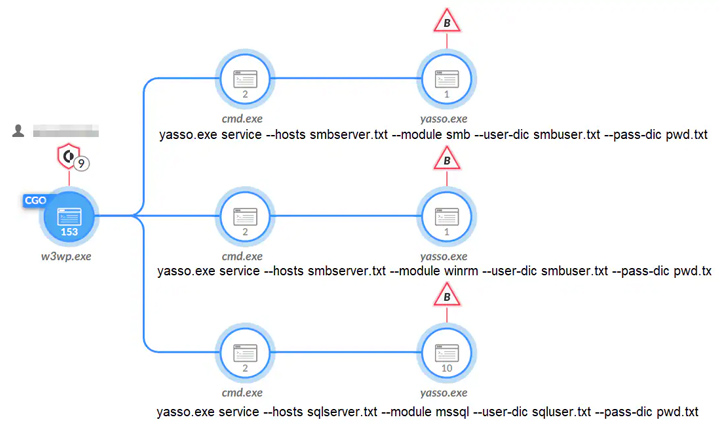
CL-STA-0043 has also been observed leveraging native Windows tools for privilege escalation, thereby enabling it to create admin accounts and run other programs with elevated privileges.
Another privilege escalation method entails the abuse of accessibility features in Windows – i.e., the “sticky keys” utility (sethc.exe) – that makes it possible to bypass login requirements and backdoor the systems.
“In the attack, the attacker usually replaces the sethc.exe binary or pointers/references to these binaries in the registry, with cmd.exe,” Rochberger explained. “When executed, it provides an elevated command prompt shell to the attacker to run arbitrary commands and other tools.”
A similar approach employing the Utility Manager (utilman.exe) to establish persistent backdoor access to a victim’s environment was documented by CrowdStrike earlier this April.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Besides using Mimikatz for credential theft, the threat actor’s modus operandi stands out for utilizing other novel methods to steal passwords, conduct lateral movement, and exfiltrate sensitive data, such as –
It’s worth pointing out that the use of Exchange PowerShell snap-ins to export mailbox data has been previously reported in the case of a Chinese state-sponsored group dubbed Silk Typhoon (formerly Hafnium), which first came to light in March 2021 in connection with the exploitation of Microsoft Exchange Server.
“This activity group’s level of sophistication, adaptiveness, and victimology suggest a highly capable APT threat actor, and it is suspected to be a nation-state threat actor,” Rochberger said.
[ad_2]
Source link