[ad_1]
Thousands of Openfire XMPP servers are unpatched against a recently disclosed high-severity flaw and are susceptible to a new exploit, according to a new report from VulnCheck.
Tracked as CVE-2023-32315 (CVSS score: 7.5), the vulnerability relates to a path traversal vulnerability in Openfire’s administrative console that could permit an unauthenticated attacker to access otherwise restricted pages reserved for privileged users.
It affects all versions of the software released since April 2015, starting with version 3.10.0. It was remediated by its developer, Ignite Realtime, earlier this May with the release of versions 4.6.8, 4.7.5, and 4.8.0.
“Path traversal protections were already in place to protect against exactly this kind of attack, but didn’t defend against certain non-standard URL encoding for UTF-16 characters that were not supported by the embedded web server that was in use at the time,” the maintainers said in a detailed advisory.

“A later upgrade of the embedded web server included support for non-standard URL encoding of UTF-16 characters. The path traversal protections in place in Openfire were not updated to include protection against this new encoding.”
As a result, a threat actor could abuse this weakness to bypass authentication requirements for admin console pages. The vulnerability has since come under active exploitation in the wild, including by attackers associated with the Kinsing (aka Money Libra) crypto botnet malware.
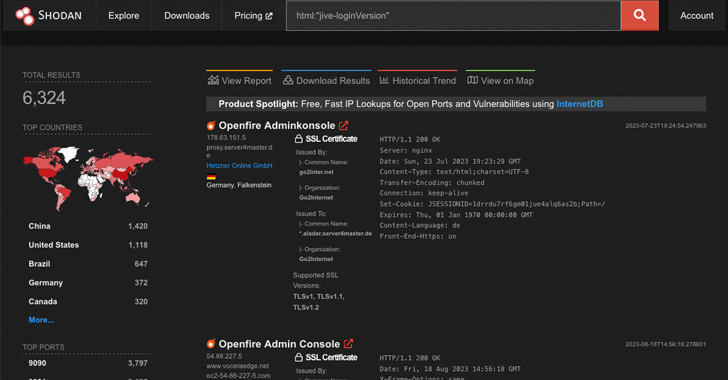
A Shodan scan conducted by the cybersecurity firm reveals that of more than 6,300 Openfire servers accessible over the internet, roughly 50% of them are running affected versions of the open-source XMPP solution.
While public exploits have leveraged the vulnerability to create an administrative user, log in, and then upload a plugin to achieve code execution, VulnCheck said it’s possible to do so without having to create an admin account, making it more stealthy and appealing for threat actors.
Elaborating on the modus operandi of the existing exploits, security researcher Jacob Baines said they involve “creating an admin user to gain access to the Openfire Plugins interface.”
“The plugin system allows administrators to add, more or less, arbitrary functionality to Openfire via uploaded Java JARs. This is, very obviously, a place to transition from authentication bypass to remote code execution.”

The improved, less noisy method devised by VulnCheck, on the other hand, employs a user-less approach that extracts the JSESSIONID and CSRF token by accessing a page called ‘plugin-admin.jsp’ and then uploading the JAR plugin via a POST request.
“Without authentication, the plugin is accepted and installed,” Baines said. “The web shell can then be accessed, without authentication, using the traversal.”
“This approach keeps login attempts out of the security audit log and prevents the ‘uploaded plugin’ notification from being recorded. That’s a pretty big deal because it leaves no evidence in the security audit log.”
The only tell-tale signs that something malicious is afoot are the logs captured in the openfire.log file, which an adversary could delete by using CVE-2023-32315, the company said.
With the vulnerability already being exploited in real-world attacks, it’s recommended that users move quickly to update to the latest versions to secure against potential threats.
[ad_2]
Source link