[ad_1]
What do basketball teams, government agencies, and car manufacturers have in common?
Each one has been breached, having confidential, proprietary, or private information stolen and exposed by insiders. In each case, the motivations and methods varied, but the risk remained the same: insiders have access to too much data with too few controls.
Insider threats continue to prove difficult for organizations to combat because — unlike an outsider — insiders can navigate sensitive data undetected and typically without suspicion.
Cybersecurity is not the first industry to tackle insider threats, however. Espionage has a long history of facing and defending against insiders by using the “CIA Triad” principles of confidentiality, integrity, and availability.
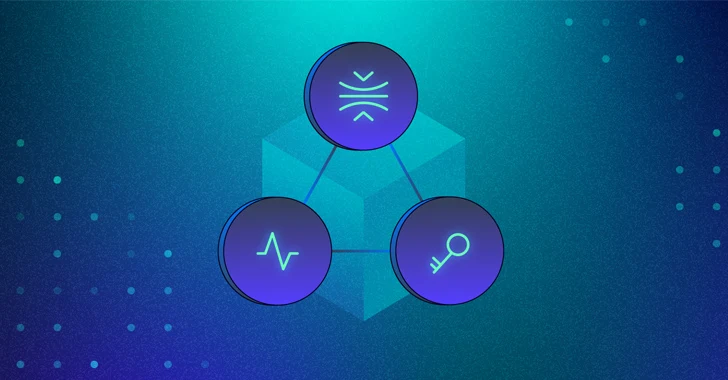
Varonis’ modern cybersecurity answer to insider risk is the data security triad of “sensitivity, access, and activity.” Using these three dimensions of data security, you can help reduce the risk and impact of an insider attack.
- Sensitivity: By understanding where your sensitive data exists, you can place controls around it to prevent unsanctioned access or exfiltration. Automated classification and labeling allow you to take an inventory of sensitive data, classify it, and apply the appropriate controls to protect it. Sensitivity dictates who, what, and how items should be accessed and what activities are allowed.
- Access: Excessive access is the crux of insider threat. Businesses today are built on collaboration and sharing, and often productivity and the availability of data trumps security. Knowing exactly who can access data and limiting that access in a way that does not impact productivity is key to mitigating risk.
- Activity: Organizations need to be able to see what actions are being taken with data, detect and respond to unusual behavior, and safely eliminate excessive access without impacting business continuity.
By combining these three pillars of the data security triad, you can effectively reduce the risk and impact of an insider attack.
Let’s look at the dimensions in more detail and see how Varonis helps with each.
Sensitivity — discovery, classification, and controls
Insiders are always going to have access to corporate data, but not all data is equally sensitive or valuable. Preventing insider risk starts by understanding which data is sensitive or regulated and which data might need additional controls.
Varonis’ built-in policies automatically discover personally identifiable information (PII), payment card information (PCI), protected health information (PHI), secrets, and more across cloud apps and infrastructure, on-prem file shares, and hybrid NAS devices. By providing a vast preconfigured rule library and easily customizable rules, Varonis helps organizations quickly discover sensitive or regulated data, intellectual property, or other org-specific data.
To apply additional controls like encryption, Varonis can label files. Using our classification results, we can find and fix files that have been misclassified by end users or not labeled at all. Correctly labeling data makes it more difficult for insiders to exfiltrate sensitive data.
Use Varonis’ classification results to find and fix files that have been misclassified by end users or not labeled at all. Easily enforce data protection policies, like encryption, with labels.
Varonis not only finds where you have sensitive data but also shows you where sensitive data is concentrated and exposed so that you can prioritize where to focus to reduce data exposure.
Access — normalization, least privilege automation, and stale data
The second pillar of the data security triad for controlling insider risk is access. Control the access to data and you control the risk of an insider. At Varonis, we call this reducing the blast radius.
This can be tricky when on day one, an average employee has access to over 17 million files and folders, while an average company has 40+ million unique permissions across SaaS applications. With how quickly data is created and shared and the amount different permissions structures vary across apps, it would take an army of admins years to understand and correct those privileges.
On top of permissions, SaaS apps have countless configurations that, if misconfigured, could open data up not only to too many internal employees, but also potentially external users or even personal accounts.
The average organization has tens of millions of unique permissions exposing critical data to too many people, the entire organization, or even the internet.
Varonis gives you a real-time view of your data security posture by combining file sensitivity, access, and activity. From shared links to nested permissions groups, misconfiguration management, and stale data, we calculate effective permissions and prioritize remediation based on risk.
To effectively limit insider threat, organizations need to not only be able to see the risk, but also remediate it.
Varonis comes with ready-made remediation policies that you can personalize for your organization. You define the guardrails and our automation will do the rest.
Varonis makes intelligent decisions about who needs access to data and who does not and can eliminate unnecessary access with least privilege automation. Because we know who is accessing data, we can remove unused access, which continually reduces the blast radius of an insider attack without human intervention and without breaking the business.
Varonis can also fix misconfigurations to prevent data from being unintentionally exposed.
Data activity is a key ingredient in determining remediation changes in order to safely to proactively limit the impact of an insider. Data activity can also help catch suspicious activity in real time.
Activity — audits, UEBA, and automated response
One of the most dangerous things about insiders is that they often do not trip alarms. They’re not going to “intrude” on your system the way an external actor would. Instead, they may silently poke around, seeing what they have access to — like in the case of the airman Jack Teixeira, who had access to confidential military documents and allegedly shared images of those documents on a Discord thread.
Organizations should be monitoring how data is accessed and shared — especially in the case of insiders — so that they can find and stop threats before damage occurs.
Varonis watches every important action on data — every read, write, create, and share — and creates behavioral baselines for what’s normal activity for each user or device. Our UEBA alerts spot threats to data, like a user accessing atypical sensitive files or sending large amounts of data to a personal email account, and can stop malicious actors in real time with automated responses.
Monitor data activity and detect threats in real time. Our threat models continuously learn and adapt to customers’ environments, spotting and stopping abnormal activity before data is compromised.
Our enriched, normalized record of every file, folder, and email activity across your cloud and on-prem environments means that you can investigate a security incident quickly using a detailed forensics log and show exactly what happened.
You can also seek help from our complimentary incident response team — a group of security architects and forensics experts available to customers and trial users — to help investigate threats.
The Varonis IR team has thwarted countless insider threats and external APTs.
In closing
Varonis’ data-centric approach to security offers organizations an unrivaled way to detect and limit the impact of insider threats proactively.
With the data security triad of “sensitivity, access, and activity,” Varonis can limit data exposure and spot threats that other solutions miss.
- Sensitivity: Varonis helps organizations quickly discover intellectual property or other org-specific data, allowing your organization to enforce data protection policies like encryption, download control, and more.
- Access: Varonis gives you a real-time view of your privileges and data security posture across cloud apps and infrastructure. Least privilege automation continually reduces your blast radius without human intervention and without breaking the business.
- Activity: Varonis creates a normalized record of every file, folder, and email activity across your cloud and on-prem environments. Our team of cybersecurity experts watches your data for threats, investigates alerts, and only surfaces true incidents that require your attention.
By combining these three pillars of the data security triad, you can effectively reduce the risk of and respond to an insider attack.
What you should do now
Below are two ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
[ad_2]
Source link