[ad_1]
Security vulnerabilities in remote desktop programs such as Sunlogin and AweSun are being exploited by threat actors to deploy the PlugX malware.
AhnLab Security Emergency Response Center (ASEC), in a new analysis, said it marks the continued abuse of the flaws to deliver a variety of payloads on compromised systems.
This includes the Sliver post-exploitation framework, XMRig cryptocurrency miner, Gh0st RAT, and Paradise ransomware. PlugX is the latest addition to this list.
The modular malware has been extensively put to use by threat actors based in China, with new features continuously added to help perform system control and information theft.
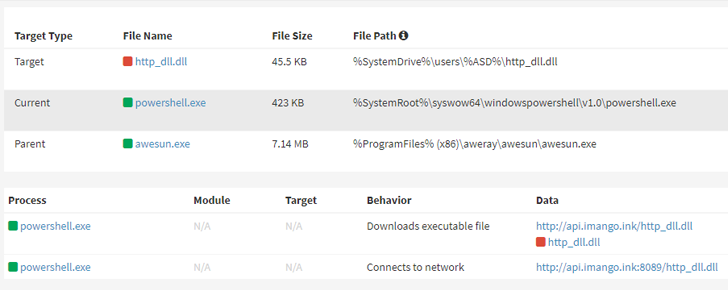
In the attacks observed by ASEC, successful exploitation of the flaws is followed by the execution of a PowerShell command that retrieves an executable and a DLL file from a remote server.
This executable is a legitimate HTTP Server Service from cybersecurity company ESET, which is used to load the DLL file by means of a technique called DLL side-loading and ultimately run the PlugX payload in memory.
“PlugX operators use a high variety of trusted binaries which are vulnerable to DLL Side-Loading, including numerous anti-virus executables,” Security Joes noted in a September 2022 report. “This has been proven to be effective while infecting victims.”
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
The backdoor is also notable for its ability to start arbitrary services, download and execute files from an external source, and drop plugins that can harvest data and propagate using Remote Desktop Protocol (RDP).
“New features are being added to [PlugX] even to this day as it continues to see steady use in attacks,” ASEC said. “When the backdoor, PlugX, is installed, threat actors can gain control over the infected system without the knowledge of the user.”
[ad_2]
Source link