[ad_1]
In recent weeks, hackers have been deploying the “IceFire” ransomware against Linux enterprise networks, a noted shift for what was once a Windows-only malware.
A report from SentinelOne published today suggests that this may represent a budding trend. Ransomware actors have been targeting Linux systems more than ever in cyberattacks in recent weeks and months, notable not least because “in comparison to Windows, Linux is more difficult to deploy ransomware against, particularly at scale,” Alex Delamotte, security researcher at SentinelOne, tells Dark Reading.
But why, if Linux makes their job more difficult, would ransomware actors be moving increasingly toward it?
The IceFire M.O.
IceFire, first discovered last March, is standard-fare ransomware aligned with other “‘big-game hunting’ (BGH) ransomware families,” Delamotte wrote. BGH ransomware is characterized by “double extortion, targeting large enterprises, using numerous persistence mechanisms, and evading analysis by deleting log files.”
But where IceFire was once an exclusively Windows-based malware, its recent attacks have taken place against Linux-based enterprise networks.
The attack flow is straightforward. Having breached a target network, the IceFire attackers steal copies of any valuable or otherwise interesting data on target machines. Only then comes the encryption. What IceFire primarily looks for are user and shared directories, as these are important yet “unprotected parts of the file system that do not require elevated privileges to write or modify,” Delamotte explained.
The attackers are careful, though. “IceFire ransomware doesn’t encrypt all files on Linux: It avoids encrypting certain paths, so that critical parts of the system are not encrypted and remain operational.”
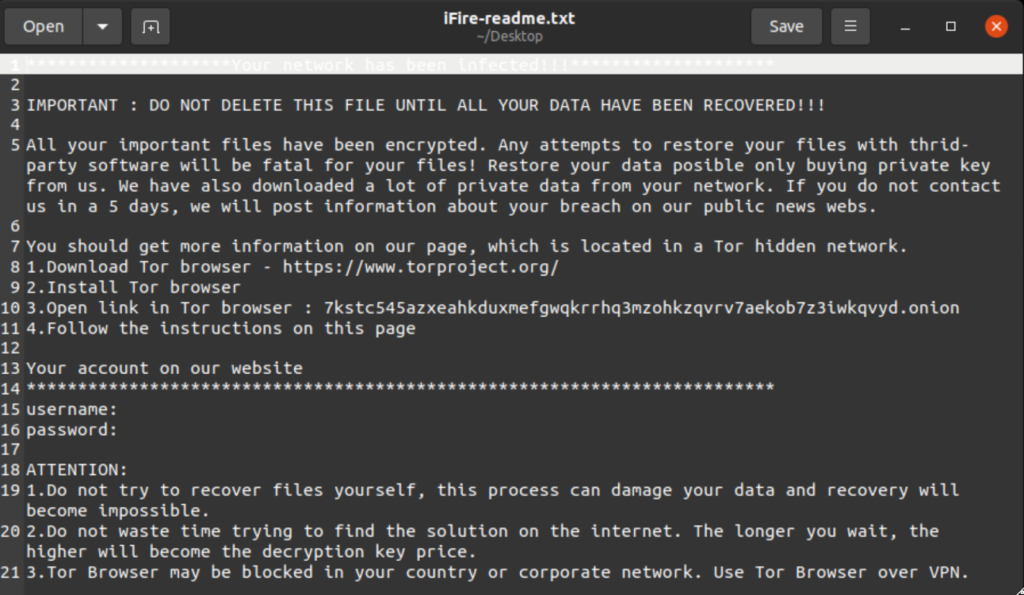
IceFire tags encrypted files with an “.ifire” extension, as many IT admin have since discovered for themselves. It also automatically drops a no-frills ransom note — “All your important files have been encrypted. Any attempts to restore your files….” The note includes a unique hardcoded username and password the victim can use to log into the attackers’ Tor-based ransom payment portal. Once the job is complete, IceFire deletes itself.
How IceFire Is Changing
Most of these details have remained consistent since IceFire’s first entry onto the scene. However, some important details have changed in recent weeks, including the victimology.
Where IceFire was once primarily used in campaigns against the healthcare, education, and technology sectors, recent attacks have focused around entertainment and media organizations, primarily in Middle Eastern countries — Iran, Pakistan, Turkey, the United Arab Emirates, and so on.
Other changes to IceFire’s M.O. derive from its operating system shift towards Linux. For example, SentinelOne has noted in the past that cyberattackers would distribute IceFire via phishing and spear-phishing emails, then use third-party, pen-test tools like Metasploit and Cobalt Strike to help it spread.
But “many Linux systems are servers,” Delamotte points out, “so typical infection vectors like phishing or drive-by download are less effective.” So instead, recent IceFire attacks have exploited CVE-2022-47986 — a critical remote code execution (RCE) vulnerability in the IBM Aspera data transfer service, with a CVSS rating of 9.8.
Why Hackers Are Targeting Linux
Delamotte posits a few reasons for why more ransomware actors are choosing Linux as of late. For one thing, she says, “Linux-based systems are frequently utilized in enterprise settings to perform crucial tasks such as hosting databases, Web servers, and other mission-critical applications. Consequently, these systems are often more valuable targets for ransomware actors due to the possibility of a larger payout resulting from a successful attack, compared to a typical Windows user.”
A second factor, she guesses, “is that some ransomware actors may perceive Linux as an unexploited market that could yield a higher return on investment.”
Finally, “the prevalence of containerization and virtualization technologies in enterprise environments has expanded the potential attack surface for ransomware actors,” she says. Many of these technologies are Linux-based, so “as ransomware groups exhaust the supply of ‘low-hanging fruit,’ they will likely prioritize these higher effort targets.”
Whatever the primary motive, if more threat actors follow in this same path, enterprises running Linux-based systems need to be ready.
Defending against ransomware requires “a multi-faceted approach,” Delamotte says, prioritizing visibility, education, insurance, multi-layered security, and patching, all at once.
“By taking a proactive approach to cybersecurity,” she says, “enterprises can increase their chances of successfully defending against ransomware attacks.”
[ad_2]
Source link